Threat Intelligence Blog

Contact us to discuss any insights from our Blog, and how we can support you in a tailored threat intelligence report.
Black Arrow Cyber Threat Briefing 05 February 2021
Black Arrow Cyber Threat Briefing 05 February 2021: Ransomware Gangs Made At Least $350 Million In 2020; Widening Security Shaped Gulf Between Firms And Remote Workers; 3.2 Billion Emails And Passwords Exposed; Account Takeover and Data Leakage Attacks Spiked In 2020; Automated Tools Increasingly Used to Launch Cyber Attacks; 93% Of Workers Overshare Online, Causing Social Engineering Risks;
Welcome to this week’s Black Arrow Cyber Threat Briefing – a weekly digest, collated and curated by our cyber experts to provide senior and middle management with an easy to digest round up of the most notable threats, vulnerabilities and cyber related news from the last week.
Top Cyber Stories of the Last Week
Ransomware Gangs Made At Least $350 Million In 2020
Ransomware gangs made at least $350 million in ransom payments last year, in 2020, blockchain analysis. The figure was compiled by tracking transactions to blockchain addresses linked to ransomware attacks. Although Chainalysis possesses one of the most complete sets of data on cryptocurrency-related cybercrime, the company said its estimate was only a lower bound of the true total due.
https://www.zdnet.com/article/ransomware-gangs-made-at-least-350-million-in-2020/
Home Working Increases Cyber Security Fears
"We see tens of different hacking attacks every single week. It is never ending."A senior computer network manager says they are bombarded from all directions. "We see everything," he says. "Staff get emails sent to them pretending to be from the service desk, asking them to reset their log-in passwords. "We see workers being tricked into downloading viruses from hackers demanding ransoms, and we have even had employees sent WhatsApp messages pretending to be from the CEO, asking for money transfers.
https://www.bbc.co.uk/news/business-55824139
3.2 Billion Emails And Passwords Exposed Online
A whopping 3.2 billion password-username pairs are up for grabs in an unnamed online hacking forum. But don't panic — the data is nothing new. It's a compilation of stolen credentials from dozens of old data breaches, some going back ten years. That doesn't mean you shouldn't be aware that your old passwords are floating out there. Yes, your passwords, and ours too. Pretty much anyone who's ever created more than three online accounts has had a password compromised by now.
https://www.tomsguide.com/news/3-2-billion-passwords-leaked
Account Takeover Attacks Spiked In 2020
Occurring whenever a bad actor can steal login credentials and seize control of an online account, takeover attacks rose from 34% of fraud detected in 2019 to 54% by the end of December 2020. Other methods of fraud were blips on the radar compared to account takeovers: The next most popular method, at just 16% of detected fraud, was money laundering/mule transactions, followed by new account fraud (14%), and a mere 12% of instances used remote access or hacking tools to accomplish their goals.
https://www.techrepublic.com/article/account-takeover-attacks-spiked-in-2020-kaspersky-says/
30% Of “Solarwinds Hack” Victims Didn’t Actually Use Solarwinds
When security last week that it had been targeted by the same attacker that compromised SolarWinds' Orion software, it noted that the attack did not use SolarWinds itself. According to Malwarebytes, the attacker had used "another intrusion vector" to gain access to a limited subset of nearly a third of the organizations attacked had no direct connection to SolarWinds.
Data Leakage Attacks Saw Huge Rise In 2020
The number of data leakage incidents grew by an “unprecedented” rate in 2020, a new report from Imperva argues. Through online means alone, not counting leaks caused by lost hardware or word of mouth, Imperva researchers tracked a 93 percent rise. By the end of the year, Imperva had identified a total of 1.7 million leaks, with the the number growing even faster in the second half of the year. Between Q3 and Q4, there was a 47 percent increase.
https://www.itproportal.com/news/data-leakage-attacks-saw-huge-rise-in-2020/
Automated Tools Increasingly Used to Launch Cyber Attacks
Cyber-criminals are increasingly making use of automation and bots to launch attacks, according to a new analysis. revealed that over half (54%) of all cyber-attacks it blocked in November and December were web application attacks which involved the use of automated tools. The most prevalent form was fuzzing attacks, making up around one in five (19.5%). This uses automation to detect and exploit the points at which applications break. This was followed by injection attacks (12%), in which cyber-criminals make use of automation tools such as sqlmap to gain access to applications.
https://www.infosecurity-magazine.com/news/automated-tools-launch-cyber/
A Second SolarWinds Hack Deepens Third-Party Software Fears
It’s been more than two months since revelations that alleged Russia-backed hackers broke into the IT management firm SolarWinds and used that access to launch a massive software supply chain attack. It now appears that Russia was not alone; Reuters reports that suspected Chinese hackers independently exploited a different flaw in SolarWinds products last year at around the same time, apparently hitting the US Department of Agriculture's National Finance Center.
https://www.wired.com/story/solarwinds-hack-china-usda/
93% Of Workers Overshare Online, Causing Security Risks
Reveals just how much, and how often, people divulge about their lives online and how attackers take advantage of it. With insights from both professionals and hackers, the report explores how cybercriminals use an abundant and seemingly cheap resource — the personal information people share on social media and in out-of-office alerts — to craft social engineering attacks.
https://www.helpnetsecurity.com/2021/02/03/workers-overshare-online/
Is There A Widening Gulf Between You And Your Remote Workers? Yes – And It’s Security Shaped
It’s been almost a year since large parts of the workforce beat a hasty retreat from their offices, and began a mass experiment in working from home, often courtesy of Microsoft 365. And after 12 or so months, it’s safe to say that the case for productive remote working has been proved, and that many workers will continue to do so even when the all clear sounds. But is there a question as to whether remote working is as secure as the traditional, office bound, hard perimeter setup? Well, yes, and it’s fair to say the jury is still very much out.
https://www.theregister.com/2021/02/04/mind_the_security_gap_regcast/
Threats
Ransomware
Blockchain Analysis Shows Connections Between Four of 2020’s Biggest Ransomware Strains
2021's First Big Ransomware Gang Launches Sleek and Bigoted 'Leak' Site
Ransomware gangs now have industrial targets in their sights. That raises the stakes for everyone
Other Social Engineering
Malware
This malware abuses Tor and Telegram infrastructure to evade detection
Tiny Kobalos malware seen backdooring SSH tools, menacing supercomputers, an ISP, and more – ESET
Experts discovered a new Trickbot module used for lateral movement
Agent Tesla ramps up its game in bypassing security walls, attacks endpoint protection
Mobile
Vulnerabilities
Data Breaches
Security firm Stormshield discloses data breach, theft of source code
Female escort review site data breach affects 470,000 members
Nation-State Actors
As usual, contact us to help assess where your risks lie and to ensure you are doing all you can do to keep you and your business secure.
Look out for our weekly ‘Cyber Tip Tuesday’ video blog and on our YouTube channel.
You can also follow us on Facebook, Twitter and LinkedIn.
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
Cyber Weekly Flash Briefing 25 September 2020: GFSC consult on new Cyber Rules; FinCEN leak exposes poor data security; Zerologon attacks detected; ransomware gang behind German hospital death
Cyber Weekly Flash Briefing 25 September 2020: GFSC consulting on new Cyber Rules; Leaked FinCEN files expose poor data security; Microsoft detects active Zerologon attacks; ransomware crew fingered for German hospital death; malware that steals your most sensitive data on the rise; Ransomware is evolving; top threats inside malicious emails; Credential Stuffing behind Recent Attacks
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
GFSC new Cyber Rules and Guidance out for consultation
The GFSC have put the Cyber Security Rules and Guidance Consultation Paper up on their website and consultation hub.
Why this matters:
The new rules and accompanying guidance came out of the 18 month thematic review which ended last year, which found that regulated financial service firms within the Bailiwick of Guernsey were not taking risks from cyber threats seriously enough and were lacking in appropriate protections and controls. These new rules seek to rectify this but many firms on the Island are going to have to do work to become compliant, especially around their ability to monitor for and detect unusual activity that could be indicative of a actual or attempted intrusion or breach.
The rules and guidance can be found here:
Leaked FinCEN files expose poor data security
Leaked documents, dubbed the “FinCEN Files,” describe global money laundering of $2 trillion processed by many of the world’s biggest banks between 2000 and 2017. The reveal illuminates the struggle for the financial industry and government to provide ironclad data protection.
“This sensational and unprecedented leak clearly demonstrates a wide spectrum of data protection weaknesses in the governmental sector, affecting even the most developed Western countries,” Ilia Kolochenko, founder and CEO of ImmuniWeb, said of the files.
“From a cybersecurity standpoint, we may expect a growing lack of trust to governmental agencies, which on one side have quasi-unlimited access to the most sensitive data of the largest organisations, while cannot duly safeguard this data on the other side,” he said.
The latest disclosure exposing apparently insufficient attempts by the public and private sectors to curb corruption came to light in a BuzzFeed News report which detailed more than 2,500 reported cases, including 2,100 Suspicious Activity Reports (SAR) filed by financial institutions with the U.S. Treasury Department’s Financial Crimes Enforcement Network (FinCEN).
JPMorgan Chase, Citigroup, Bank of America, Deutsche Bank, HSBC and Standard Chartered are among the financial institutions cited in the leaked files as processing dirty money around the world. The documents may have come from a whistleblower or insider at FinCEN. The International Consortium of Investigative Journalists (ICIJ), which represents 108 news organizations in 88 countries, is conducting a probe of the matter.
Why this matters:
Other similar investigative reports on similar wrongdoing focused single financial, tax or legal institutions, such as the 2017 Panama Papers emanating from clients of the law firm Mossack Fonseca. But the FinCEN docs reveal that a wide array of people from oligarchs and corrupt politicians to drug dealers and organised crime throughout the world know how to circumvent the system’s supposed checks and balances.
Read more: https://www.scmagazine.com/home/security-news/leaked-fincen-files-expose-poor-data-security/
Microsoft says it detected active attacks leveraging Zerologon vulnerability
Hackers are actively exploiting the Zerologon vulnerability in real-world attacks, Microsoft's security intelligence team said this week.
The attacks were expected to happen, according to security industry experts.
Multiple versions of weaponized proof-of-concept exploit code have been published online in freely downloadable form since details about the Zerologon vulnerability were revealed a week ago.
The first proof-of-concept exploit was published hours after the explanatory blog post, confirming initial analysis that the Zerologon bug is easy to exploit, even by low-skilled threat actors.
Why this matters:
Put simply the Zerologon bug is a vulnerability in Netlogon, the protocol used by Windows systems to authenticate against a Windows Server running as a domain controller. Exploiting the Zerologon bug can allow hackers to take over the domain controller, and inherently a company's internal network.
Zerologon was described by many as the most dangerous bug revealed this year. US federal agencies were given three days to patch domain controllers or disconnect them from federal networks.
As several security experts have recommended since Microsoft revealed the attacks, companies that have their domain controller exposed on the internet should take systems offline to patch them.
These internet-reachable servers are particularly vulnerable as attacks can be mounted directly, without the hacker first needing a foothold on internal systems.
Doppelpaymer ransomware crew fingered for attack on German hospital that caused death of a patient
The Doppelpaymer ransomware gang were behind the cyber-attack on a German hospital that led to one patient's death, according to local sources.
A German newspaper carried a report that Doppelpaymer's eponymous ransomware had been introduced to the University Hospital Düsseldorf's network through a vulnerable Citrix product.
That ransomware infection, activated last week, is said by local prosecutors to have led to the death of one patient who the hospital was unable to treat on arrival. She died in an ambulance while being transported to another medical facility with functioning systems.
Why this matters:
According to a report handed to the provincial government of North Rhine-Westphalia and seen by the German Press Association (DPA), the ransomware's loader had been lurking on the hospital's network since December 2019, the same month a patch was issued by Citrix for CVE-2019-19781 – the same vuln exploited to hit the hospital.
Whilst this is the first time a loss of life has been directly attributed to ransomware the threats are increasing all the time.
Vulnerabilities must be patched as soon as possible to stop known vulnerabilities from being used in attacks.
Read more: https://www.theregister.com/2020/09/23/doppelpaymer_german_hospital_ransomware/
“LokiBot,” the malware that steals your most sensitive data, is on the rise
Agencies in the US have reported seeing a big uptick in infections coming from LokiBot, an open source DIY malware package for Windows that’s openly sold or traded for free in underground forums. It steals passwords and cryptocurrency wallets, and it can also download and install new malware.
The increase was measured by an automated intrusion-detection system for collecting, correlating, analysing, and sharing computer security information.
US cyber agency CISA observed a notable increase in the use of LokiBot malware by malicious cyber actors since July 2020 according to an alert issued this week.
Why this matters:
While not quite as prevalent or noxious as the Emotet malware, LokiBot remains a serious and widespread menace. The infostealer spreads through a variety of methods, including malicious email attachments, exploitation of software vulnerabilities, and trojans sneaked into pirated or free apps. Its simple interface and reliable codebase make it attractive to a wide range of crooks, including those who are new to cybercrime and have few technical skills.
Ransomware is evolving, but the key to preventing attacks remains the same
Ransomware attacks are getting more aggressive according to a senior figure at Europe's law enforcement agency, but there are simple steps which organisations can follow to protect themselves – and their employees – from falling victim to attacks.
"Ransomware is one of the main threats," said the head of operations at Europol's European Cybercrime Centre (EC3). Europol supports the 27 EU member states in their fight against terrorism, cybercrime and other serious and organised forms of crime.
"Criminals behind ransomware attacks are adapting their attack vectors, they're more aggressive than in the past – they're not only encrypting the files, they're also exfiltrating data and making it available," he explained. "From a law enforcement perspective, we have been monitoring this evolution."
Why this matters:
This year has seen a rise in ransomware attacks where cyber criminals aren't just encrypting the networks of victims and demanding six-figure bitcoin payment to return the files, but they're also threatening to publish sensitive corporate information and other stolen data if the victim doesn't pay the ransom.
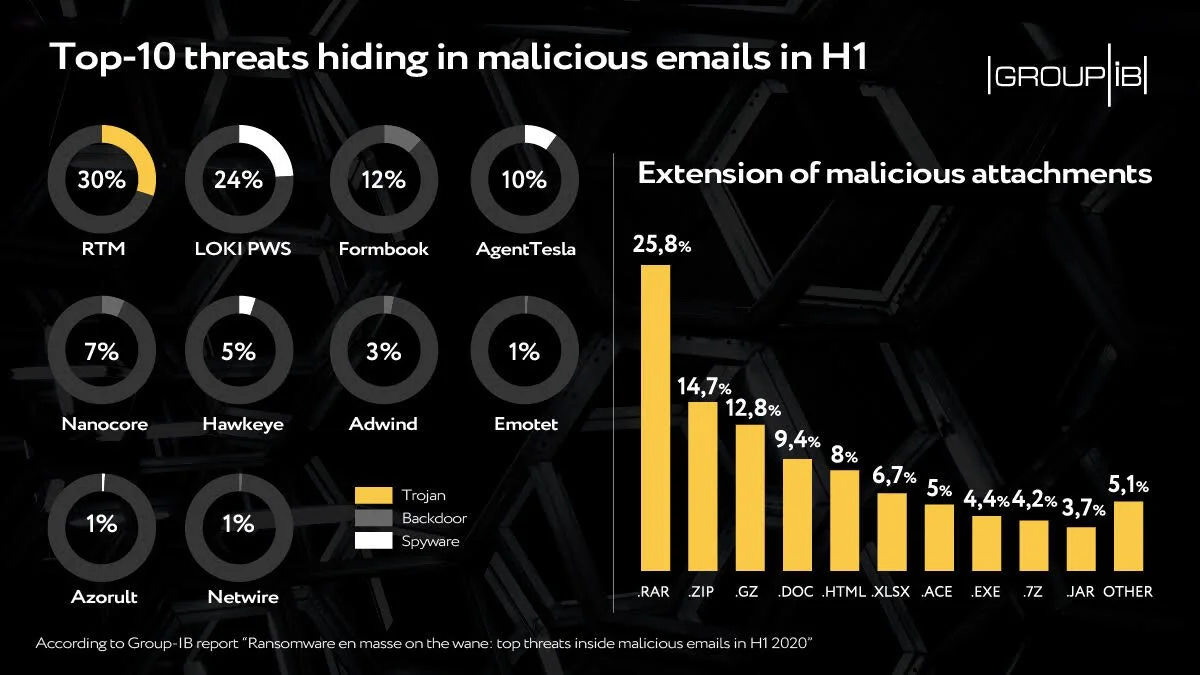
A look at the top threats inside malicious emails
Web-phishing targeting various online services almost doubled during the COVID-19 pandemic: it accounted for 46 percent of the total number of fake web pages, Group-IB reveals.
Ransomware, the headliner of the previous half-year, walked off stage: only 1 percent of emails analysed contained this kind of malware. Every third email, meanwhile, contained spyware, which is used by threat actors to steal payment data or other sensitive info to then put it on sale in the darknet or blackmail its owner.
Downloaders, intended for the installation of additional malware, and backdoors, granting cybercriminals remote access to victims’ computers, also made it to top-3. They are followed by banking Trojans, whose share in the total amount of malicious attachments showed growth for the first time in a while.
According to the data, in H1 2020 detected malicious emails were:
43 percent of the malicious mails had attachments with spyware or links leading to their downloading
17 percent contained downloaders
16 percent had backdoors
15 percent had banking trojans
Ransomware, which in the second half of 2019 hid in every second malicious email, almost disappeared from the mailboxes in the first six months of this year with a share of less than 1 percent.
Why this matters:
These findings confirm adversaries’ growing interest in Big Game Hunting. Ransomware operators have switched from attacks en masse on individuals to corporate networks. Thus, when attacking large companies, instead of infecting the computer of a separate individual immediately after the compromise, attackers use the infected machine to move laterally in the network, escalate the privileges in the system and distribute ransomware on as many hosts as possible.
Read more: https://www.helpnetsecurity.com/2020/09/21/top-threats-inside-malicious-emails/
Credential Stuffing: the Culprit of Recent Attacks
A year ago, researchers found that 2.2 billion leaked records, known as Collection 1-5, were being passed around by hackers. This ‘mega leak’ included 1.2 billion unique email addresses and password combinations, 773 million unique email addresses and 21 million plaintext passwords. With this treasure trove, hackers can simply test email and password combinations on different sites, hoping that a user has reused one. This popular technique is known as credential stuffing and is the culprit of many recent data breaches.
There are only a few months left of 2020 but this year has seen its fair share of major data breaches including:
Marriott International experienced another mega breach, when it was still recovering from the 2018 data breach that exposed approximately 339 million customer records
Zoom became a new favourite for hackers due to the remote working mandated in many parts of the world - in early April Zoom fell victim to a credential stuffing attack, which resulted in 500,000 of Zoom’s usernames and passwords being exposed on the Dark Web.
GoDaddy, the world’s largest domain registrar confirmed in April that credentials of 28,000 of its customer web hosting accounts were compromised in a security incident back in October 2019.
Nintendo - in March, users reported unauthorised logins to their accounts and charges for digital items without their permission. In June Nintendo advised that approximately 300,000 accounts were affected by the breach, resulting in the compromise of personal identifiable information such as email address, date of birth, country and gender.
Why this matters:
It has become evident that many of the recent data breaches were the result of credential stuffing attacks leveraging compromised passwords or passphrases. Credential stuffing attacks are automated hacks where stolen usernames and password combinations are thrown at the login process of various websites in an effort to break in. With billions of compromised credentials already circulating the Dark Web, credential stuffing attacks can be carried out with relative ease and with a 1-3% success rate.
When the account of an employee is compromised, hackers can gain access to sensitive data that organisation has collected, and sell it on the Dark Web. The stolen data, often including login credentials, can then be used to infiltrate other organisations’ systems which creates a never-ending cycle.
This is why the LinkedIn breach was blamed for several secondary compromises due to users recycling their exposed LinkedIn passwords on other sites.
Read more: https://www.infosecurity-magazine.com/blogs/credential-stuffing-recent-attacks/