Threat Intelligence Blog

Contact us to discuss any insights from our Blog, and how we can support you in a tailored threat intelligence report.
The next open Cyber User Education and Awareness Training session with any availability left is on Wednesday 06 October 2021 from 10am-12pm.
The next open Cyber User Education and Awareness Training session with any availability left is on Wednesday 06 October 2021 from 10am-12pm.
The next open Cyber User Education and Awareness Training session with any availability left is on Wednesday 06 October 2021 from 10am-12pm.
We currently have 4 spaces remaining and the cost per delegate is £150.
Firms can send between 1-14 staff to these open training courses meaning less disruption to business operations and new starters, for example, don't need to wait until the next time the whole firm gets cyber training.
These open courses are run at least once per week so we can offer a lot of flexibility.
Remember only with Black Arrow do you get access to world-class cyber security experts from British Intelligence, Defence, Law Enforcement, Big-4 Advisory, FTSE100, Global Financial Services and the GFSC.
Call us on 711 988 or email training@blackarrowcyber.com to book places for your staff members.
Black Arrow Cyber Threat Briefing 10 September 2021
Black Arrow Cyber Threat Briefing 10 September 2021
-91% Of IT Teams Have Felt 'Forced' To Trade Security For Business Operations
-Ransomware Attacks Increased Exponentially In 2021
-One In Three Suspect Phishing Emails Reported By Employees Really Are Malicious
-Hackers Shift From Malware To Credential Hijacking
-Attacker Breakout Time Now Less Than 30 Minutes
-Hackers Leak VPN Account Passwords From 87,000 Fortinet FortiGate Devices
-The Impact Of Ransomware On Cyber Insurance Driving The Need For Broader Cyber Security Knowledge
-Hackers Exploit Camera Vulnerabilities To Spy On Parents
-39% Of All Internet Traffic Is From Bad Bots
Welcome to this week’s Black Arrow Cyber Threat Briefing – a weekly digest, collated and curated by our cyber experts to provide senior and middle management with an easy to digest round up of the most notable threats, vulnerabilities, and cyber related news from the last week.
Top Cyber Stories of the Last Week
91% Of IT Teams Have Felt 'Forced' To Trade Security For Business Operations
A new survey suggests that most IT staff have felt pressured to ignore security concerns in favour of business operations. On Thursday, a new study report was released, which combines data from an online YouGov survey targeting office workers that adopted WFH and global research conducted with IT decision-makers. In total, 91% of those surveyed said that they have felt "pressured" to compromise security due to the need for business continuity during the COVID-19 pandemic. 76% of respondents said that security had taken a backseat, and furthermore, 83% believe that working from home has created a "ticking time bomb" for corporate security incidents. https://www.zdnet.com/article/91-of-it-teams-have-felt-forced-to-trade-security-for-business-operations/
Ransomware Attacks Increased Exponentially In 2021
The growing threat of ransomware has been highlighted by NCC Group's Research Intelligence and Fusion Team (RIFT) analysis. Between January-March 2021 and April-June 2021, the number of ransomware assaults studied by the team climbed by 288%, indicating that enterprises are still facing waves of digital extortion in the form of targeted ransomware. https://www.ehackingnews.com/2021/09/ransomware-attacks-increased.html
Phishing Attacks: One In Three Suspect Emails Reported By Employees Really Are Malicious
All the time spent ticking boxes in cyber security training sessions seems to be paying off after all: according to a new report, about a third of emails reported by employees really are malicious or highly suspect, demonstrating the effectiveness of the well-established maxim "Think before you click". Researchers analysed over 200,000 emails that were flagged by employees from organisations across the globe in the first half of 2021 and found that 33% of the reports could be classified as phishing. https://www.zdnet.com/article/phishing-attacks-one-in-three-suspect-emails-reported-by-employees-really-are-malicious/
Hackers Shift From Malware To Credential Hijacking
Adversaries are relying less on malware to conduct attacks that are consequently more difficult to detect, according to an annual report conducted by researchers. “According to data from our customer base indexed by Threat Graph, 68% of detections from the last three months were not malware-based,” reads the report released Wednesday. “Attackers are increasingly attempting to accomplish their objectives without writing malware to the endpoint, using legitimate credentials and built-in tools (living off the land)—which are deliberate efforts to evade detection by traditional antivirus products.” https://www.nextgov.com/cybersecurity/2021/09/report-hackers-shift-malware-credential-hacking/185209/
Attacker Breakout Time Now Less Than 30 Minutes
The average time it takes threat actors to move from initial access to lateral movement has fallen by 67% over the past year, putting extra pressure on security operations (SecOps) teams, according to researchers. The findings come from researchers own investigations with customers across around 248,000 unique global endpoints. For incidents where this “breakout time” could be derived over the past year, it averaged just 1 hour 32 minutes. However, in over a third (36%) of intrusions, adversaries managed to move laterally to additional hosts in under 30 minutes. https://www.infosecurity-magazine.com/news/attacker-breakout-time-now-less/
Hackers Leak VPN Account Passwords From 87,000 Fortinet FortiGate Devices
Network security solutions provider Fortinet confirmed that a malicious actor had unauthorizedly disclosed VPN login names and passwords associated with 87,000 FortiGate SSL-VPN devices. "These credentials were obtained from systems that remained unpatched at the time of the actor's scan. While they may have since been patched, if the passwords were not reset, they remain vulnerable," the company said in a statement on Wednesday. https://thehackernews.com/2021/09/hackers-leak-vpn-account-passwords-from.html
53% Find It Difficult To Prevent An Insider Attack During Data Aggregation
Recent data from researchers found that 53% of companies find it impossible or very difficult to prevent an insider attack when data is being aggregated, a key indicator of intent of an attack. The vast majority of security threats follow a pattern or sequence of activity leading up to an attack, and insider threats are no exception. To fully understand any insider incident, visibility into the entire kill chain of an attack is imperative to preventing the exfiltration of critical data. https://venturebeat.com/2021/09/02/53-find-it-difficult-to-prevent-an-insider-attack-during-data-aggregation/
The Impact Of Ransomware On Cyber Insurance Driving The Need For Broader Cyber Security Knowledge
Not only have ransomware attacks spiked, the amount of ransom demanded has grown exponentially—to somewhere between $50 and $70 million dollars. Cyber Insurers can’t cover “whatever amount the hacker demands”—so major policies lost money. Insurers have responded by raising premiums, restricting coverage, or even getting out of the cyber-insurance game altogether in vulnerable markets. https://www.helpnetsecurity.com/2021/09/10/cyber-insurance-ransomware/
Hackers Exploit Camera Vulnerabilities To Spy On Parents
Various zero day vulnerabilities in home baby monitor could be compromised that lets threat actors hack into camera feed and put malicious codes like malware. The security issues were found in the IoT gadgets, made by China based developer Victure, that were found by researchers. In a security report, researchers revealed about the stack-based buffer flaw present in ONVIF server Victure PC420 component camera that allows hackers to plant remote codes on the victim device. When compromised, hacker can discover cameras (not owned by them) and command devices to broadcast camera feeds to third party and exploit the camera firmware. https://www.ehackingnews.com/2021/09/hackers-exploit-camera-vulnerabilities.html
39% Of All Internet Traffic Is From Bad Bots
Automated traffic takes up 64% of internet traffic – and whilst just 25% of automated traffic was made up by good bots, such as search engine crawlers and social network bots, 39% of all traffic was from bad bots, a Barracuda report reveals.
These bad bots include both basic web scrapers and attack scripts, as well as advanced persistent bots. These advanced bots try their best to evade standard defences and attempt to perform their malicious activities under the radar. The report revealed that the most common of these persistent bots were ones that went after e-commerce applications and login portals. https://www.helpnetsecurity.com/2021/09/07/bad-bots-internet-traffic/
Threats
Ransomware
BEC
Phishing
Other Social Engineering
Malware
Traffic Exchange Networks Distributing Malware Disguised As Cracked Software
New Malware Uses Novel Fileless Technique To Evade Detection
Mobile
IOT
Vulnerabilities
Zoho ManageEngine Password Manager Zero-Day Gets A Fix, Amid Attacks
New CPU Side-Channel Attack Takes Aim At Chrome’s Site Isolation Feature
Microsoft, CISA Urge Mitigations For Zero-Day RCE Flaw In Windows
Atlassian CISO Defends Company's Confluence Vulnerability Response, Urges Patching
PoC Released For GhostScript Vulnerability That Exposed Airbnb, Dropbox
New 0-Day Attack Targeting Windows Users With Microsoft Office Documents
Cisco Patches Critical Authentication Bug With Public Exploit
Data Breaches/Leaks
Organised Crime & Criminal Actors
Cryptocurrency/Cryptojacking
Insider Threats
DoS/DDoS
Nation State Actors
Cloud
Privacy
Other News
OWASP Shakes Up Web App Threat Categories With Release Of Draft Top 10
A Zero-Trust Future: Why Cyber Security Should Be Prioritized For The Hybrid Working World
Microsoft Has A $20 Billion Hacking Plan, But Cyber Security Has A Big Spending Problem
Misbehaving Microsoft Teams Ad Brings Down The Entire Windows 11 Desktop
This Seemingly Normal Lightning Cable Will Leak Everything You Type
HSE Cyber Attack: Irish Health Service Still Recovering Months After Hack
As usual, contact us to help assess where your risks lie and to ensure you are doing all you can do to keep you and your business secure.
Look out for our weekly ‘Cyber Tip Tuesday’ video blog and on our YouTube channel.
You can also follow us on Facebook, Twitter and LinkedIn.
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
Guernsey regulated financial services firms - are you ready to evidence compliance with the new GFSC Cyber Rules? - Guernsey Press 04 September 2021
Time’s up. Are you ready to evidence compliance with the new GFSC Cyber Rules now in effect?
Time’s up. Are you ready to evidence compliance with the new GFSC Cyber Rules now in effect?
Guernsey Regulated Financial Services Firms, the deadline for compliance with the GFSC Cyber Rules is today!
Guernsey Regulated Financial Services Firms, the deadline for compliance with the GFSC Cyber Rules is today!
Will you be ready to explain your strategy and governance when the GFSC turn up for a regulatory visit?
The Cyber Rules compel Boards to take accountability for Cyber risks where previously it may have belonged to IT. Technology is only one piece of the puzzle, and often it is your people that present your weakest link.
We support our clients with an independent and proportionate gap analysis report that assesses risks and controls across people, operations and technology. This informs the strategy and governance that shows the GFSC what they want to see, reinforced by objective education and awareness for Boards and users.
Guernsey Regulated Financial Services Firms, the deadline for compliance with the GFSC Cyber Rules is today!
Will you be ready to explain your strategy and governance when the GFSC turn up for a regulatory visit?
The Cyber Rules compel Boards to take accountability for Cyber risks where previously it may have belonged to IT. Technology is only one piece of the puzzle, and often it is your people that present your weakest link.
We support our clients with an independent and proportionate gap analysis report that assesses risks and controls across people, operations and technology. This informs the strategy and governance that shows the GFSC what they want to see, reinforced by objective education and awareness for Boards and users.
We help our clients get the best performance from their IT Provider, to see and remediate the risks that cannot be revealed in a self-assessment either by the provider or the client.
Talk to the professionals today, with the experience and qualifications you can count on.
Contact us on contact@blackarrowcyber.com or call us on 711988
Our latest piece in the Guernsey Press - The new GFSC Cyber Security Rules: What the GFSC demands of firms, and why leaving it all to your IT provider won't make you compliant
Our latest piece in the Guernsey Press - The new GFSC Cyber Security Rules: What the GFSC demands of firms, and why leaving it all to your IT provider won't make you compliant
New Cyber Rules just released by the GFSC - and how Black Arrow can help you become compliant
Welcome to this week's Black Arrow Cyber Tip Tuesday, this week Tony is talking about the new cyber rules that the GFSC have just released and which are now in force for regulated financial services firms in the Bailiwick.
The GFSC have now released the new cyber rules and all regulated financial will need to be able to demonstrate compliance with these new regulations.
The regulations are built around compliance or adherence to the internationally recognised NIST cyber security framework and the five pillars contained therein, being identify, protect, detect, respond and recover.
We can assist any firm by producing a gap analysis against the NIST standard, and therefore the GFSC rules, to identify any areas of non-compliance or areas where firms will need to bolster their existing security arrangements.
Remember that cyber and information encompasses a lot more than just IT but is rather requires a holistic approach across people, operations and technology.
Leaving this solely to your IT team or IT provider likely won’t provide the coverage the GFSC now expects from firms.
Remember too taking a proactive approach should always be about preventing an attack or breach, many firms do not survive a significant cyber event, and for those that do recovery invariably costs a lot more than it would have cost to put appropriate controls in place to prevent the breach happening in the first place.
Boards are expected to show good governance over cyber and information security as they would be expected to do with any older and longer established risks.
It is clear from the new rules that the GFSC also agree that the responsibility for cyber and information security clearly sits with Boards, not IT.
Talk to us today to see how we can help you demonstrate compliance or become compliant with the new GFSC cyber rules.
Welcome to this week's Black Arrow Cyber Tip Tuesday, this week Tony is talking about the new cyber rules that the GFSC have just released and which are now in force for regulated financial services firms in the Bailiwick.
The GFSC have now released the new cyber rules and all regulated financial will need to be able to demonstrate compliance with these new regulations.
The regulations are built around compliance or adherence to the internationally recognised NIST cyber security framework and the five pillars contained therein, being identify, protect, detect, respond and recover.
We can assist any firm by producing a gap analysis against the NIST standard, and therefore the GFSC rules, to identify any areas of non-compliance or areas where firms will need to bolster their existing security arrangements.
Remember that cyber and information encompasses a lot more than just IT but is rather requires a holistic approach across people, operations and technology.
Leaving this solely to your IT team or IT provider likely won’t provide the coverage the GFSC now expects from firms.
Remember too taking a proactive approach should always be about preventing an attack or breach, many firms do not survive a significant cyber event, and for those that do recovery invariably costs a lot more than it would have cost to put appropriate controls in place to prevent the breach happening in the first place.
Boards are expected to show good governance over cyber and information security as they would be expected to do with any older and longer established risks.
It is clear from the new rules that the GFSC also agree that the responsibility for cyber and information security clearly sits with Boards, not IT.
Talk to us today to see how we can help you demonstrate compliance or become compliant with the new GFSC cyber rules.
Cyber Weekly Flash Briefing 25 September 2020: GFSC consult on new Cyber Rules; FinCEN leak exposes poor data security; Zerologon attacks detected; ransomware gang behind German hospital death
Cyber Weekly Flash Briefing 25 September 2020: GFSC consulting on new Cyber Rules; Leaked FinCEN files expose poor data security; Microsoft detects active Zerologon attacks; ransomware crew fingered for German hospital death; malware that steals your most sensitive data on the rise; Ransomware is evolving; top threats inside malicious emails; Credential Stuffing behind Recent Attacks
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
GFSC new Cyber Rules and Guidance out for consultation
The GFSC have put the Cyber Security Rules and Guidance Consultation Paper up on their website and consultation hub.
Why this matters:
The new rules and accompanying guidance came out of the 18 month thematic review which ended last year, which found that regulated financial service firms within the Bailiwick of Guernsey were not taking risks from cyber threats seriously enough and were lacking in appropriate protections and controls. These new rules seek to rectify this but many firms on the Island are going to have to do work to become compliant, especially around their ability to monitor for and detect unusual activity that could be indicative of a actual or attempted intrusion or breach.
The rules and guidance can be found here:
Leaked FinCEN files expose poor data security
Leaked documents, dubbed the “FinCEN Files,” describe global money laundering of $2 trillion processed by many of the world’s biggest banks between 2000 and 2017. The reveal illuminates the struggle for the financial industry and government to provide ironclad data protection.
“This sensational and unprecedented leak clearly demonstrates a wide spectrum of data protection weaknesses in the governmental sector, affecting even the most developed Western countries,” Ilia Kolochenko, founder and CEO of ImmuniWeb, said of the files.
“From a cybersecurity standpoint, we may expect a growing lack of trust to governmental agencies, which on one side have quasi-unlimited access to the most sensitive data of the largest organisations, while cannot duly safeguard this data on the other side,” he said.
The latest disclosure exposing apparently insufficient attempts by the public and private sectors to curb corruption came to light in a BuzzFeed News report which detailed more than 2,500 reported cases, including 2,100 Suspicious Activity Reports (SAR) filed by financial institutions with the U.S. Treasury Department’s Financial Crimes Enforcement Network (FinCEN).
JPMorgan Chase, Citigroup, Bank of America, Deutsche Bank, HSBC and Standard Chartered are among the financial institutions cited in the leaked files as processing dirty money around the world. The documents may have come from a whistleblower or insider at FinCEN. The International Consortium of Investigative Journalists (ICIJ), which represents 108 news organizations in 88 countries, is conducting a probe of the matter.
Why this matters:
Other similar investigative reports on similar wrongdoing focused single financial, tax or legal institutions, such as the 2017 Panama Papers emanating from clients of the law firm Mossack Fonseca. But the FinCEN docs reveal that a wide array of people from oligarchs and corrupt politicians to drug dealers and organised crime throughout the world know how to circumvent the system’s supposed checks and balances.
Read more: https://www.scmagazine.com/home/security-news/leaked-fincen-files-expose-poor-data-security/
Microsoft says it detected active attacks leveraging Zerologon vulnerability
Hackers are actively exploiting the Zerologon vulnerability in real-world attacks, Microsoft's security intelligence team said this week.
The attacks were expected to happen, according to security industry experts.
Multiple versions of weaponized proof-of-concept exploit code have been published online in freely downloadable form since details about the Zerologon vulnerability were revealed a week ago.
The first proof-of-concept exploit was published hours after the explanatory blog post, confirming initial analysis that the Zerologon bug is easy to exploit, even by low-skilled threat actors.
Why this matters:
Put simply the Zerologon bug is a vulnerability in Netlogon, the protocol used by Windows systems to authenticate against a Windows Server running as a domain controller. Exploiting the Zerologon bug can allow hackers to take over the domain controller, and inherently a company's internal network.
Zerologon was described by many as the most dangerous bug revealed this year. US federal agencies were given three days to patch domain controllers or disconnect them from federal networks.
As several security experts have recommended since Microsoft revealed the attacks, companies that have their domain controller exposed on the internet should take systems offline to patch them.
These internet-reachable servers are particularly vulnerable as attacks can be mounted directly, without the hacker first needing a foothold on internal systems.
Doppelpaymer ransomware crew fingered for attack on German hospital that caused death of a patient
The Doppelpaymer ransomware gang were behind the cyber-attack on a German hospital that led to one patient's death, according to local sources.
A German newspaper carried a report that Doppelpaymer's eponymous ransomware had been introduced to the University Hospital Düsseldorf's network through a vulnerable Citrix product.
That ransomware infection, activated last week, is said by local prosecutors to have led to the death of one patient who the hospital was unable to treat on arrival. She died in an ambulance while being transported to another medical facility with functioning systems.
Why this matters:
According to a report handed to the provincial government of North Rhine-Westphalia and seen by the German Press Association (DPA), the ransomware's loader had been lurking on the hospital's network since December 2019, the same month a patch was issued by Citrix for CVE-2019-19781 – the same vuln exploited to hit the hospital.
Whilst this is the first time a loss of life has been directly attributed to ransomware the threats are increasing all the time.
Vulnerabilities must be patched as soon as possible to stop known vulnerabilities from being used in attacks.
Read more: https://www.theregister.com/2020/09/23/doppelpaymer_german_hospital_ransomware/
“LokiBot,” the malware that steals your most sensitive data, is on the rise
Agencies in the US have reported seeing a big uptick in infections coming from LokiBot, an open source DIY malware package for Windows that’s openly sold or traded for free in underground forums. It steals passwords and cryptocurrency wallets, and it can also download and install new malware.
The increase was measured by an automated intrusion-detection system for collecting, correlating, analysing, and sharing computer security information.
US cyber agency CISA observed a notable increase in the use of LokiBot malware by malicious cyber actors since July 2020 according to an alert issued this week.
Why this matters:
While not quite as prevalent or noxious as the Emotet malware, LokiBot remains a serious and widespread menace. The infostealer spreads through a variety of methods, including malicious email attachments, exploitation of software vulnerabilities, and trojans sneaked into pirated or free apps. Its simple interface and reliable codebase make it attractive to a wide range of crooks, including those who are new to cybercrime and have few technical skills.
Ransomware is evolving, but the key to preventing attacks remains the same
Ransomware attacks are getting more aggressive according to a senior figure at Europe's law enforcement agency, but there are simple steps which organisations can follow to protect themselves – and their employees – from falling victim to attacks.
"Ransomware is one of the main threats," said the head of operations at Europol's European Cybercrime Centre (EC3). Europol supports the 27 EU member states in their fight against terrorism, cybercrime and other serious and organised forms of crime.
"Criminals behind ransomware attacks are adapting their attack vectors, they're more aggressive than in the past – they're not only encrypting the files, they're also exfiltrating data and making it available," he explained. "From a law enforcement perspective, we have been monitoring this evolution."
Why this matters:
This year has seen a rise in ransomware attacks where cyber criminals aren't just encrypting the networks of victims and demanding six-figure bitcoin payment to return the files, but they're also threatening to publish sensitive corporate information and other stolen data if the victim doesn't pay the ransom.
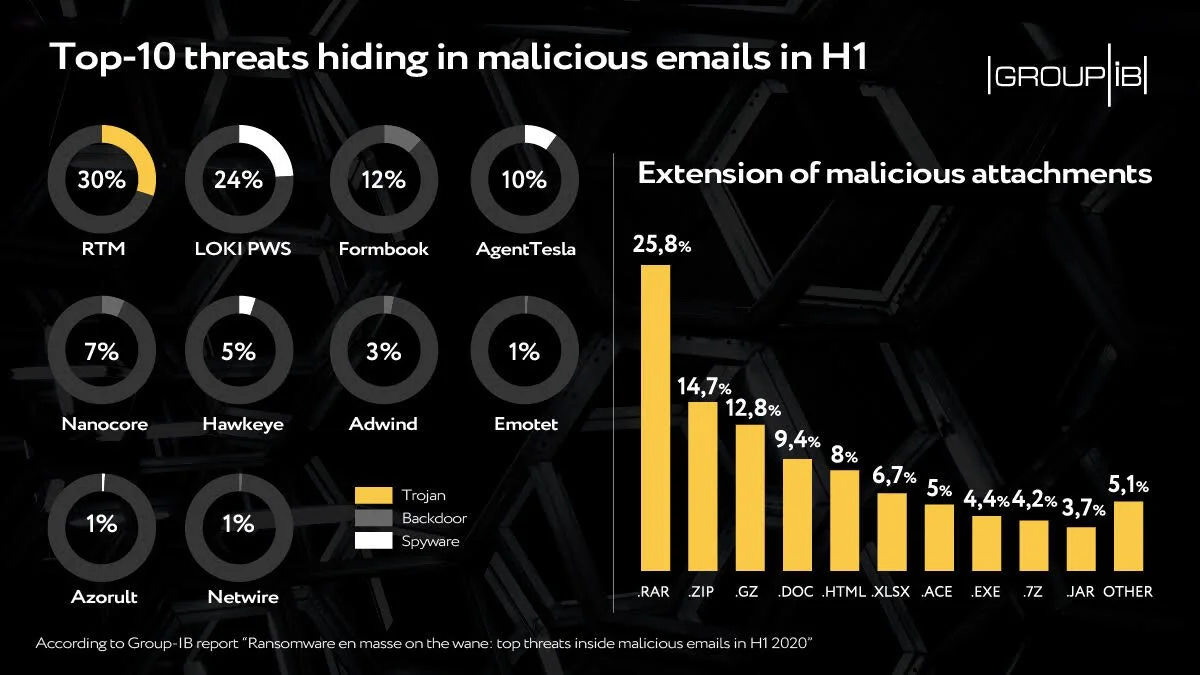
A look at the top threats inside malicious emails
Web-phishing targeting various online services almost doubled during the COVID-19 pandemic: it accounted for 46 percent of the total number of fake web pages, Group-IB reveals.
Ransomware, the headliner of the previous half-year, walked off stage: only 1 percent of emails analysed contained this kind of malware. Every third email, meanwhile, contained spyware, which is used by threat actors to steal payment data or other sensitive info to then put it on sale in the darknet or blackmail its owner.
Downloaders, intended for the installation of additional malware, and backdoors, granting cybercriminals remote access to victims’ computers, also made it to top-3. They are followed by banking Trojans, whose share in the total amount of malicious attachments showed growth for the first time in a while.
According to the data, in H1 2020 detected malicious emails were:
43 percent of the malicious mails had attachments with spyware or links leading to their downloading
17 percent contained downloaders
16 percent had backdoors
15 percent had banking trojans
Ransomware, which in the second half of 2019 hid in every second malicious email, almost disappeared from the mailboxes in the first six months of this year with a share of less than 1 percent.
Why this matters:
These findings confirm adversaries’ growing interest in Big Game Hunting. Ransomware operators have switched from attacks en masse on individuals to corporate networks. Thus, when attacking large companies, instead of infecting the computer of a separate individual immediately after the compromise, attackers use the infected machine to move laterally in the network, escalate the privileges in the system and distribute ransomware on as many hosts as possible.
Read more: https://www.helpnetsecurity.com/2020/09/21/top-threats-inside-malicious-emails/
Credential Stuffing: the Culprit of Recent Attacks
A year ago, researchers found that 2.2 billion leaked records, known as Collection 1-5, were being passed around by hackers. This ‘mega leak’ included 1.2 billion unique email addresses and password combinations, 773 million unique email addresses and 21 million plaintext passwords. With this treasure trove, hackers can simply test email and password combinations on different sites, hoping that a user has reused one. This popular technique is known as credential stuffing and is the culprit of many recent data breaches.
There are only a few months left of 2020 but this year has seen its fair share of major data breaches including:
Marriott International experienced another mega breach, when it was still recovering from the 2018 data breach that exposed approximately 339 million customer records
Zoom became a new favourite for hackers due to the remote working mandated in many parts of the world - in early April Zoom fell victim to a credential stuffing attack, which resulted in 500,000 of Zoom’s usernames and passwords being exposed on the Dark Web.
GoDaddy, the world’s largest domain registrar confirmed in April that credentials of 28,000 of its customer web hosting accounts were compromised in a security incident back in October 2019.
Nintendo - in March, users reported unauthorised logins to their accounts and charges for digital items without their permission. In June Nintendo advised that approximately 300,000 accounts were affected by the breach, resulting in the compromise of personal identifiable information such as email address, date of birth, country and gender.
Why this matters:
It has become evident that many of the recent data breaches were the result of credential stuffing attacks leveraging compromised passwords or passphrases. Credential stuffing attacks are automated hacks where stolen usernames and password combinations are thrown at the login process of various websites in an effort to break in. With billions of compromised credentials already circulating the Dark Web, credential stuffing attacks can be carried out with relative ease and with a 1-3% success rate.
When the account of an employee is compromised, hackers can gain access to sensitive data that organisation has collected, and sell it on the Dark Web. The stolen data, often including login credentials, can then be used to infiltrate other organisations’ systems which creates a never-ending cycle.
This is why the LinkedIn breach was blamed for several secondary compromises due to users recycling their exposed LinkedIn passwords on other sites.
Read more: https://www.infosecurity-magazine.com/blogs/credential-stuffing-recent-attacks/