Threat Intelligence Blog

Contact us to discuss any insights from our Blog, and how we can support you in a tailored threat intelligence report.
Black Arrow Cyber Threat Briefing 06 November 2020
Cyber Threat Briefing 06 November 2020
Welcome to this week’s Black Arrow Cyber Threat Briefing – a weekly digest of open source intelligence (OSINT), collated and curated by our cyber experts to provide senior and middle management with an easy to digest round up of the most notable threats, vulnerabilities and cyber related news from the last week.
Top Cyber Headlines of the Week
2020 could be 'the worst year in cyber security history'
Businesses around the world are severely unprepared to face the sheer scale of cyber threats facing us today, new research has claimed.
The latest 2020 Business Threat Landscape report from security firm Bitdefender has said that this could be the worst year in cyber security history, as despite multiple warnings, many firms still aren't ready to protect themselves.
Bitdefender's report found that the "new normal" of remote working had led many businesses to face difficulties in ensuring their online protection, with 50% of organisations "completely unprepared" to face a scenario in which they had to migrate their entire workforce in a working from home environment.
https://www.techradar.com/news/2020-could-be-the-worst-year-in-cybersecurity-history
Two-Thirds of Financial Services Firms Suffered Cyber-Attack in the Past Year
Almost two-thirds (65%) of large financial services companies have suffered a cyber attack in the past year, while 45% have experienced a rise in attack attempts since the start of the COVID-19 pandemic.
This is according to new research from HelpSystems, which surveyed 250 CISOs and CIOs in global financial services firms about the impact of the pandemic on their cybersecurity.
It highlighted that these organisations are taking cybersecurity increasingly seriously, with 92% stating that they have increased investment in this area over the past 12 months, with 26% doing so by a significant amount. The main targets of this investment have included secure file transfer (64%), protecting the remote workforce (63%) and cloud/office365 (56%).
https://www.infosecurity-magazine.com/news/two-thirds-financial-services/
Proofpoint survey: IT security leaders worry about and are ill-prepared to defeat cyber-attacks
IT security leaders say they are ill-prepared for a cyber attack and believe that human error and a lack of security awareness are major risk factors for their organisations, according to a series of reports and surveys from cyber security vendor Proofpoint. But there are some marked variations in both the rates and the types of cyber attack between the regions surveyed.
It’s a dynamic attack landscape: in the DACH countries of Germany, Austria and Switzerland 67 per cent of IT security leaders say they have suffered at least one attack in the last 12 months, while in Benelux 72 per cent of respondents say their business has suffered at least one cyber attack in the same time period. In Sweden 59 per cent of businesses have been attacked at least once, while in the UAE the figure is much higher at 82 per cent - with 51 per cent of IT security leaders in the UAE saying their business has been targeted multiple times.
https://www.theregister.com/2020/11/05/proofpoint_survey_it_security_leaders/
Akamai sees doubling in malicious internet traffic as remote world’s bad actors boom, too
Akamai Technologies’ CEO said he is impressed by the amazing traffic levels on the internet during the coronavirus pandemic, and the world technology infrastructure’s ability to handle it. But during the stay-at-home boom, the web and cyber security expert also has been closely watching a boom in bad actors.
With so many people working from home, hackers are taking advantage, and massively increasing the number of attacks as daily routine changes caused by the pandemic are prolonged, and become potentially permanent.
“I think the threat actors are trying to take advantage of the pandemic, and of course, the prize is greater now that so much business has moved online”
Quarter-over-quarter — Akamai reported its Q3 results this week — the cyber security and cloud computing company has tracked a doubling of malicious traffic as telecommuting makes for easier targets.
Attacks Against Microsoft’s Remote Desktop Protocol Soar Under Work From Home Measures
The number of Remote Desktop Protocol (RDP) attacks soared by 140% in Q3 compared with the previous quarter, as cyber criminals looked to take advantage of companies relying on remote access while working from home.
RDP makes it possible for one computer to connect to another over a network and control it as though the individual was sat at the keyboard themselves. While the Microsoft tool is useful for businesses and popular among IT administrators, it has increasingly been targeted by hackers who try to gain administrator access to company servers. Once inside they are able to disable security software, steal files, delete data and install malicious software.
Slovak internet security firm ESET detected the surge between July and September, with the number of separate companies reporting brute-force attacks against their RDP connection increasing by 37% quarter-over-quarter.
Threats
Ransomware
Ransomware gangs that steal your data don't always delete it
Ransomware gangs that steal a company's data and then get paid a ransom fee to delete it don't always follow through on their promise.
The number of cases where something like this has happened has increased, according to a report published by Coveware this week and according to several incidents shared by security researchers with ZDNet researchers over the past few months.
https://www.zdnet.com/article/ransomware-gangs-that-steal-your-data-dont-always-delete-it/
Spike in Emotet activity could mean big payday for ransomware gangs
There's been a massive increase in Emotet attacks and cyber criminals are taking advantage of machines compromised by the malware to launch more malware infections as well as ransomware campaigns.
The October 2020 HP-Bromium Threat Insights Report reports a 1,200% increase in Emotet detections from July to September compared to the previous three months in which deployment of the malware appeared to decline.
https://www.zdnet.com/article/spike-in-emotet-activity-could-mean-big-payday-for-ransomware-gangs/
Italian beverage vendor Campari knocked offline after ransomware attack
Campari Group, the famed Italian beverage vendor behind brands like Campari, Cinzano, and Appleton, has been hit by a ransomware attack and has taken down a large part of its IT network.
The attack took place last Sunday, on November 1, and has been linked to the RagnarLocker ransomware gang, according to a copy of the ransom note shared with ZDNet by a malware researcher who goes online by the name of Pancak3.
Hackney Council still working to restore services as IT boss describes horror at cyber attack
Hackney’s director of information communication technology (ICT) Rob Miller was playing football with his family on a Sunday morning early in October when he got a message letting him know there was a systems outage being investigated at the Town Hall.
By the end of Sunday, the council had moved swiftly to shut down its systems, declared an emergency and notified national agencies after Miller’s team found “clear markers” that the local authority had been hit by a serious cyber attack.
Leading toy maker Mattel hit by ransomware
Toy industry giant Mattel disclosed that they suffered a ransomware attack in July that impacted some of its business functions but did not lead to data theft.
Mattel is the second-largest toymaker in the world with 24,000 employees and $5.7 billion in revenue for 2019. Mattel is known for its popular brands, including Barbie, Hot Wheels, Fisher-Price, American Girl, and Thomas & Friends.
https://www.bleepingcomputer.com/news/security/leading-toy-maker-mattel-hit-by-ransomware/
Business Email Compromise (BEC)
BEC attacks increase in most industries, invoice and payment fraud rise by 155%
BEC attacks increased 15% quarter-over-quarter, driven by an explosion in invoice and payment fraud, Abnormal Security research reveals.
“As the industry’s only measure of BEC attack volume by industry, our quarterly BEC research is important for CISOs to prepare and stay ahead of attackers,” said Evan Reiser, CEO of Abnormal Security.
“Not only are BEC campaigns continuing to increase overall, they are rising in 75% of industries that we track. Since these attacks are targeted and sophisticated, these increases could indicate an ability for threat actors to scale that may overwhelm some businesses.”
For this research, BEC campaigns across eight major industries were tracked, including retail/consumer goods and manufacturing, technology, energy/infrastructure, services, medical, media/tv, finance and hospitality.
https://www.helpnetsecurity.com/2020/11/03/bec-attacks-increase-quarter-over-quarter/
Phishing
Sneaky Office 365 phishing inverts images to evade detection
A creative Office 365 phishing campaign has been inverting images used as backgrounds for landing pages to avoid getting flagged as malicious by crawlers designed to spot phishing sites.
These inverted backgrounds are commonly used as part of phishing kits that attempt to clone legitimate login pages as closely as possible to harvest a target's credentials by tricking them into entering them into a fake login form.
The BBC Experiences Over 250,000 Malicious Email Attacks Per Day
The British Broadcasting Corporation (BBC), the UK’s public service broadcaster, faces in excess of a quarter of a million malicious email attacks every day, according to data obtained following a Freedom of Information (FoI) request.
The corporation blocked an average of 283,597 malicious emails per day during the first eight months of 2020.
According to the data, every month the BBC receives an average of 6,704,188 emails that are classified as scam or spam as well as 18,662 malware attacks such as viruses, ransomware and spyware. In total, 51,898,393 infected emails were blocked in the period from January to August 2020.
The month which contained the highest amount of recorded incidents was July, when the BBC received 6,787,635 spam and 13,592 malware attempts. The next highest was March, when the COVID-19 first struck the UK, with 6,768,632 spam emails and 14,089 malware attacks.
https://www.infosecurity-magazine.com/news/bbc-experiences-malicious-email/
Malware
US Cyber Command exposes new Russian malware
US Cyber Command has exposed eight new malware samples that were developed and deployed by Russian hackers in recent attacks
Six of the eight samples are for the ComRAT malware (used by the Turla hacking group), while the other two are samples for the Zebrocy malware (used by the APT28 hacking group).
Both ComRAT and Zebrocy are malware families that have been used by Russia hacking groups for years, with ComRAT being deployed in attacks for more than a decade, having evolved from the old Agent.BTZ malware.
https://www.zdnet.com/article/us-cyber-command-exposes-new-russian-malware/
IoT
New data shows just how badly home users overestimate IoT security
A new survey from the National Cyber Security Alliance (NCSA) shows adult workers vastly overestimate the security of the internet devices in their homes.
The survey polled 1,000 adults – 500 aged 18-34 and 500 aged 50-75 – and found that the overwhelming majority of both believed the internet of things devices they owned were secure.
IoT devices, particularly those that are cheap, outdated and hard to upgrade, are widely considered to be an easy target for hackers. Yet 87 percent of the younger group and 77 percent of the older group said they were either “somewhat” or “very confident” in the security of their connected things
Vulnerabilities
Windows 10 zero-day could allow hackers to seize control of your computer
A security bug has been discovered that affects every version of the Windows operating system, from Windows 7 to Windows 10. The vulnerability can be found within the Windows Kernel Cryptography Driver and enables attackers to gain admin-level control of a victim’s computer.
The flaw was discovered by Google’s Project Zero security team, which subsequently notified Microsoft. The Redmond-based firm was given seven days to patch the bug before Google published further details – a task that proved beyond the company.
Adobe warns Windows, MacOS users of critical acrobat and reader flaws
Adobe has fixed critical-severity flaws tied to four CVEs in the Windows and macOS versions of its Acrobat and Reader family of application software services. The vulnerabilities could be exploited to execute arbitrary code on affected products.
These critical flaws include a heap-based buffer overflow, out-of-bounds write glitch and two use-after free flaws. The bugs are part of Adobe’s regularly scheduled patches, which overall patched critical-, important- and moderate-severity vulnerabilities tied to 14 CVEs.
https://threatpost.com/adobe-windows-macos-critical-acrobat-reader-flaws/160903/
Zero-day in Cisco AnyConnect Secure Mobility Client yet to be fixed
Cisco has disclosed a zero-day vulnerability, in the Cisco AnyConnect Secure Mobility Client software with the public availability of a proof-of-concept exploit code.
The flaw resided in the inter-process communication (IPC) channel of Cisco AnyConnect Client, it can be exploited by authenticated and local attackers to execute malicious scripts via a targeted user.
Critical bug actively used to deploy Cobalt Strike on Oracle servers
Threat actors are actively exploiting Oracle WebLogic servers unpatched against CVE-2020-14882 to deploy Cobalt Strike beacons which allow for persistent remote access to compromised devices.
Cobalt Strike is a legitimate penetration testing tool also used by threat actors in post-exploitation tasks and to deploy so-called beacons that enable them to gain persistent remote access.
This later allows them to access the compromised servers to harvest data and to deploy second stage malware payloads.
Oracle Solaris Zero-Day Attack Revealed
A previously known threat group, called UNC1945, has been compromising telecommunications companies and targeting financial and professional consulting industries, by exploiting a security flaw in Oracle’s Solaris operating system.
Researchers said that the group was exploiting the bug when it was a zero-day, long before a patch arrived.
The bug, was recently addressed in Oracle’s October 2020 Critical Patch Update. The vulnerability exists in the Oracle Solaris Pluggable Authentication Module (PAM) and allows an unauthenticated attacker with network access via multiple protocols to exploit and compromise the operating system. Threat actors utilized a remote exploitation tool, which researchers call “EVILSUN,” to exploit the flaw.
https://threatpost.com/oracle-solaris-zero-day-attack/160929/
Data Breaches
Marriott Hotels fined £18.4m for data breach that hit millions
The UK's data privacy watchdog has fined the Marriott Hotels chain £18.4m for a major data breach that may have affected up to 339 million guests.
The Information Commissioner's Office (ICO) said names, contact information, and passport details may all have been compromised in a cyber-attack.
The breach included seven million guest records for people in the UK.
The ICO said the company failed to put appropriate safeguards in place but acknowledged it had improved.
https://www.bbc.co.uk/news/technology-54748843
23,600 hacked databases have leaked from a defunct 'data breach index' site
More than 23,000 hacked databases have been made available for download on several hacking forums and Telegram channels in what threat intel analysts are calling the biggest leak of its kind.
The database collection is said to have originated from Cit0Day.in, a private service advertised on hacking forums to other cybercriminals.
Cit0day operated by collecting hacked databases and then providing access to usernames, emails, addresses, and even cleartext passwords to other hackers for a daily or monthly fee.
Cybercriminals would then use the site to identify possible passwords for targeted users and then attempt to breach their accounts at other, more high-profile sites.
Other News
Deloitte's 'Test your Hacker IQ' site fails itself after exposing database user name, password in config file
Suspended sentence for bank IT worker who hacked his boss's webcam because he didn't get a payrise
APT Groups Finding Success with Mix of Old and New Tools
Quantum computing may make current encryption obsolete, a quantum internet could be the solution
Reports Published in the Last Week
NCSC defends UK from more than 700 cyber attacks while supporting national pandemic response
The NCSC's fourth Annual Review reveals its ongoing work against cyber attacks, support for the UK during the coronavirus pandemic.
https://www.ncsc.gov.uk/news/ncsc-defends-uk-700-cyber-attack-national-pandemic
Ransomware Demands continue to rise as Data Exfiltration becomes common, and Maze subdues
The Coveware Quarterly Ransomware Report describes ransomware incident response trends during Q3 of 2020. Ransomware groups continue to leverage data exfiltration as a tactic, though trust that stolen data will be deleted is eroding as defaults become more frequent when exfiltrated data is made public despite the victim paying. In Q3, Coveware saw the Maze group sunset their operations as the active affiliates migrated to Egregor (a fork of Maze). We also saw the return of the original Ryuk group, which has been dormant since the end of Q1.
https://www.coveware.com/blog/q3-2020-ransomware-marketplace-report
As usual, contact us to help assess where your risks lie and to ensure you are doing all you can do to keep you and your business secure.
Look out for our weekly ‘Cyber Tip Tuesday’ video blog and on our YouTube channel.
You can also follow us on Facebook, Twitter and LinkedIn.
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
Cyber Threat Briefing 16 October 2020: ransomware tidal wave; notable ransomware victims from the last week; BEC Attacks: Nigeria no longer epicentre, losses top $26B; Trickbot back; MS fix 87 vulns
Cyber Threat Briefing 16 October 2020: ransomware tidal wave of attacks; Notable ransomware victims of the last week; BEC Attacks: Nigeria No Longer the Epicentre as Losses top $26B; Trickbot back after disruption attempts; Microsoft October 2020 Patch Tuesday fixes 87 vulnerabilities; Malware gangs love open source offensive hacking tools
Welcome to this week’s Black Arrow Cyber Threat Briefing – a weekly digest, collated and curated by our cyber experts to provide senior and middle management with an easy to digest round up of the most notable threats, vulnerabilities and cyber related news from the last week.
Threats
Ransomware
Ransomware is growing and growing and getting worse all the time, with the G7 this week warning of ‘a tidal wave of ransomware attacks’ [source]. It is fast approaching becoming such a problem that it may soon reach epidemic status with few organisations left unaffected as firm after firm falls victim.
The ransomware gangs have turned crime into a multi-million pound business empire, it is estimated that $7.5 billion was extorted from victims last year in the United States alone [source], putting any legitimate industry or business sector to shame in term of meteoric growth. This is not small scale actors working out of their bedrooms, they have customer support centres and 24/7 helplines, they have plush offices and flash cars, paid for by the victims of their crimes, paid for by firms like yours paying ransoms.
And here's how attackers are getting in: in nearly half (47%) of ransomware cases gangs used the open remote desktop protocol, a tool that has been used by many companies to help staff work from home, but which can also give attackers a way in if it is not correctly secured.
More than a quarter (26%) of cases were traced back to a phishing email, and a smaller number used specific vulnerability exploits (17%), including Citrix NetScaler CVE-2019-19781 and Pulse VPN CVE-2019-11510. This was followed by account takeovers, at 10%. [source]
Criminal gangs have earned so much money and power they are now outsourcing much of the labour, allowing them to live of their spoils while their empires continue to grow, while they do next to nothing, with more and more joining their ranks [source]
As long as even a small number of victims pay the ransom this remains highly lucrative for attackers.
The ransom for Software AG is $23m, but they will demand much smaller sums from much smaller firms – so how are they doing this? Are larger firms being specifically targeted with tailored phishing campaigns, where they hope they will get lucky in getting an employee to fall for the bait, where lower value targets are being hit with machine/algorithmic generated phishing attacks, with lower levels of sophistication and more of a ‘spray and pray’ approach, hoping casting a wide enough net will still result in larger numbers of lower value victims.
We keep trying to warn firms how bad this is getting, and we don’t do this to drum up business, we do this because we are hugely concerned about the direction this is going and how damaging this can be for any firm.
Many firms are reluctant to take cyber security seriously, believing it won’t happen to them, but it is happening to firm after firm after firm who believed it wouldn’t happen to them. It’s too late to start thinking about what you should have done after you’ve become a victim, it’s far better, and far cheaper, to take steps to avoid being a victim in the first place than trying to recover or pay the ransom.
Of the increasing number of firms that do go hit, many don’t survive, and those that do often find things are never the same again, with impacts on confidence levels in your staff and in your IT and information security departments [source]
Ransomware is not only affecting desktops, laptops and servers, but also now increasingly Android and other mobile platforms [source]
Protecting against ransomware is not a luxury or something that can kicked down the road to look at another day, firms need to ensure they are protecting themselves against this threat now – before they become a victim.
Notable ransomware victims of the last week
There have been a number of high profile victims of ransomware in the last week, notably Software AG, a German conglomerate with operations in more than 70 countries, which was attacked by the Clop group who are threatening to dump stolen data if the $23 million ransom is not paid.
Carnival Cruises were hit with ransomware affecting data and personal information for guests, employees and crew for Carnival Cruises, Holland America and Seabourn as well as casino operations.
Early indications point to the disruption being experiences by Hackney Council with their systems stemming from a ransomware attack, although this has not been confirmed.
BEC
BEC Attacks: Nigeria No Longer the Epicentre as Losses top $26B
Business Email Compromise (BEC) Fraudsters now have bases of operation across at least 39 countries and are responsible for $26 billion in losses annually, and growing.
A study of more than 9,000 instances of BEC attacks all over the world shows that the number has skyrocketed over the past year, and that the social-engineering scam has expanded well beyond its historic roots in Nigeria.
Why this matters:
A recent report entitled The Global Reach of Business Email Compromise, found that these attacks cost businesses a staggering $26 billion every year. And that trend appears to be accelerating. In fact, researchers found BEC attacks currently make up a full 40 percent of cyber crime losses globally, impacting at least 177 countries.
For context, the Anti-Phishing Working Group recently find that the average wire transfer in a BEC scan is around $80,000.
In a BEC attack, a scammer impersonates a company executive or other trusted party and tries to trick an employee responsible for payments or other financial transactions into writing money to a bogus account. Attackers usually conduct a fair amount of recon work, studying executive styles and uncovering the organisations vendors, billing system practices and other information to help mount a convincing attack.
Read more: https://threatpost.com/bec-attacks-nigeria-losses-snowball/160118/
Trickbot back after disruption attempts
The Trickbot botnet looks to be working once again, despite separate efforts in the past few weeks aimed at disrupting its operation.
Earlier this month the Emotet spam botnet – which is often the precursor to TrickBot being loaded onto a system – began receiving spam templates intended for mass distribution. These spam templates contained Microsoft Word document attachments with malicious macros that fetch and load a copy of Emotet onto the victim machine. The Emotet bot reached out to its controllers and received commands to download and execute Trickbot on victim machines.
The Trickbot group tag that researchers identified is tied to a typical infection campaign that information security researchers have been observing for the past 6 months or more.
Additionally, Intel 471 researchers saw an update to the Trickbot plugin server configuration file. Fifteen server addresses were added, and two old servers were retained in the configuration, along with the server’s ‘.onion’ address. This was likely done as a fix that would help operators maintain that their infrastructure remains operational. [link]
Why this matters:
The fix is another round in the back-and-forth between Trickbot’s operators and the separate public and private sector parties that have attempted to disrupt the botnet’s actions. This includes actions by the US Cyber Command and Microsoft, who issued a public statement that it had taken legal action to “combat ransomware ahead of U.S. elections.” The legal action involved Microsoft attempting to disrupt a number of Trickbot command and control server IP addresses in the United States.
The fact that Trickbot has resumed normal operations despite the best efforts of the likes of the US Cyber Command and Microsoft shows how resilient of an operation Trickbot is, and how much more effort is needed to fully take the botnet offline for good. The botnet’s operators have all the IT support of legitimate enterprises – continuity planning, backups, automated deployment, and a dedicated workforce – that allow them to quickly react to disruptive measures.
Read more: https://public.intel471.com/blog/trickbot-online-emotet-microsoft-cyber-command-disruption-attempts/
Vulnerabilities
Microsoft October 2020 Patch Tuesday fixes 87 vulnerabilities
Microsoft this week released its monthly batch of security updates known as Patch Tuesday, and this month the OS maker has patched 87 vulnerabilities across a wide range Microsoft products.
By far, the most dangerous bug patched this month is CVE-2020-16898. Described as a remote code execution (RCE) vulnerability in the Windows TCP/IP stack, this bug can allow attackers to take over Windows systems by sending malicious ICMPv6 Router Advertisement packets to an unpatched computer via a network connection.
Another bug to keep an eye on is CVE-2020-16947, a remote code execution issue in Outlook. Microsoft says this bug can be exploited by tricking a user to open a specially crafted file with an affected version of Microsoft Outlook software. [source1] [source2]
Why this matters:
The bug was discovered internally by Microsoft engineers, and OS versions vulnerable to CVE-2020-16898 include Windows 10 and Windows Server 2019.
With a severity score of 9.8 out of a maximum 10, Microsoft considers the bug dangerous and likely to be weaponised, and rightfully so.
Patching the bug is recommended, but workarounds such as disabling ICMPv6 RDNSS support also exist, which would allow system administrators to deploy temporary mitigations until they quality-test this month’s security updates for any OS-crashing bugs.
Critical SonicWall VPN Portal Bug Allows DoS, Worming RCE
A critical security bug in the SonicWall VPN Portal can be used to crash the device and prevent users from connecting to corporate resources. It could also open the door to remote code execution (RCE), researchers said.
The flaw (CVE-2020-5135) is a stack-based buffer overflow in the SonicWall Network Security Applicance (NSA). According to researchers who discovered it, the flaw exists within HTTP/HTTPS service used for product management and SSL VPN remote access. [source]
Why this matters:
An unskilled attacker could trigger a persistent denial-of-service condition using an unauthenticated HTTP request involving a custom protocol handler.
Adding insult to injury, this particular flaw exists in a pre-authentication routine, and within a component (SSL VPN) which is typically exposed to the public internet.
‘More Than A Billion’ Phone Wide Open To ‘Backdoor’ Remote Code Execution in Adtech Company’s Code
Malicious code impacting more than a billion smartphone owners is currently in the wild and enabling remote code execution. [source]
Why this matters:
Remote code execution is a very serious security violation, and basically enables the owner of that code do almost anything they want on your phone.
Miscellaneous Cyber News of the Weeks
Malware gangs love open source offensive hacking tools
In the cyber security field, the term OST (Open Source Tools) refers to software apps, libraries, and exploits that possess offensive hacking capabilities and have been released as either free downloads or under an open source license.
OST projects are usually released to provide a proof-of-concept exploit for a new vulnerability, to demonstrate a new (or old) hacking technique, or as penetration testing utilities shared with the community.
These discussions have been taking place for more than a decade. However, they have always been based on personal experiences and convictions, and never on actual raw data.
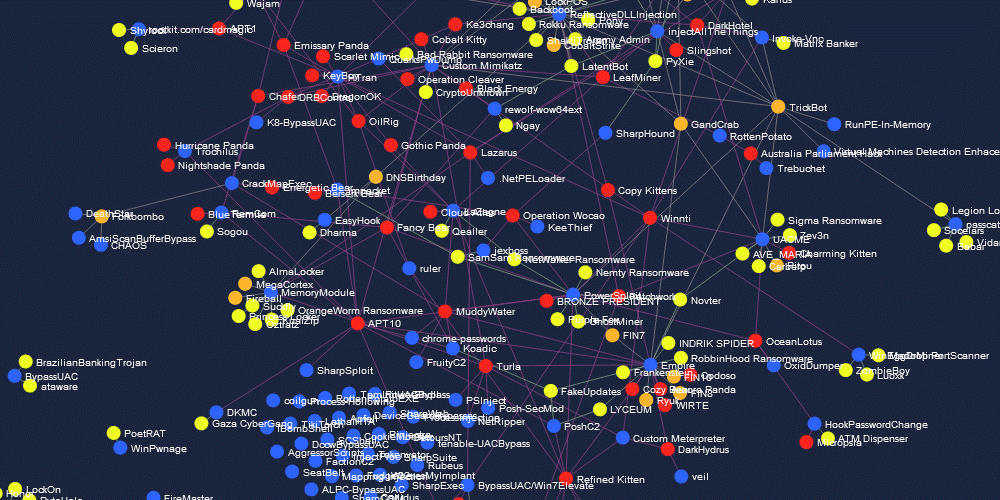
That changed this week when a security researcher compiled data on 129 open source offensive hacking tools and searched through malware samples and cyber-security reports to discover how widespread was the adoption of OST projects among hacking groups — such as low-level malware gangs, elite financial crime groups, and even nation-state sponsored APTs. [source]
The results were compiled in an interactive map – available here
Why this matters:
Today, OST is one of the most (if not the most) controversial topics in the information security community.
On one side, you have the people who are in favour of releasing such tools, arguing that they can help defenders learn and prepare systems and networks for future attacks.
On the opposing side, you have the ones who say that OST projects help attackers reduce the costs of developing their own tools and hiding activities into a cloud of tests and legitimate pen-tests.
Fitbit Spyware Steals Personal Data via Watch Face
A researcher has found they can take advantage of lax Fitbit privacy controls to build a malicious spyware watch face.
A wide-open app-building API (Application Programming Interface) could allow an attacker to build a malicious application that could access Fitbit user data, and send it to any server.
A proof-of-concept was created to do just that, after realizing that Fitbit devices are loaded with sensitive personal data. [source]
Why this matters:
Essentially, the API could send device type, location and user information including gender, age, height, heart rate and weight and it could also access calendar information. While this doesn’t include PII profile data, the calendar invites could expose additional information such as names and locations.
The researcher was able to make the app available through the Fitbit Gallery (where Fitbit showcases various third-party and in-house apps). Thus, the spyware appears legitimate, and increase the likelihood it would be downloaded.
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
As usual, contact us to help assess where your risks lie and to ensure you are doing all you can do to keep you and your business secure.
Look out for our weekly ‘Cyber Tip Tuesday’ video blog and on our YouTube channel.