Threat Intelligence Blog

Contact us to discuss any insights from our Blog, and how we can support you in a tailored threat intelligence report.
Black Arrow Cyber Threat Briefing 25 December 2020
Black Arrow Cyber Threat Briefing 25 December 2020: The Cyber Threat Is Real and Growing; Ransomware Attacks Surge in Q3; In 2021 there will be a cyber attack every 11 seconds; The West has suffered a massive cyber breach and it's hard to overstate how bad it is; Big tech companies including Intel, Nvidia, and Cisco were all infected during the SolarWinds hack
Welcome to this week’s Black Arrow Cyber Threat Briefing – a weekly digest, collated and curated by our cyber experts to provide senior and middle management with an easy to digest round up of the most notable threats, vulnerabilities and cyber related news from the last week.
Top Cyber Headlines of the Week
The Cyber Threat Is Real and Growing
The SolarWinds breach could be one of the most significant cyber incidents in history. Russian intelligence—likely the SVR, the foreign-intelligence branch—infiltrated and sat undetected on U.S. and other government networks for nearly 10 months. It was a sophisticated, smart and savvy attack that should alarm the public and private sectors.
We may not know the full extent of the damage for some time. Don’t be surprised if more government entities disclose that they too were victims of this attack. Don’t be surprised either if it emerges that private companies were hit. SolarWinds says it has more than 300,000 customers, including 400 companies in the Fortune 500. That’s a lot of potential victims.
https://www.wsj.com/articles/the-cyber-threat-is-real-and-growing-11608484291
Ransomware Attacks Surge in Q3 as Cyber Criminals Shift Tactics
A record growth in ransomware attacks took place in Q3 of 2020 compared to Q2, from 39% to 51% of all malware attempts according to a new study. The study also found that hacking accounted for 30% of all attacks during Q3, with cyber criminals reducing their emphasis on social engineering tactics compared with earlier this year. The researchers noted that the percentage of social engineering attacks using COVID-19 as a lure fell from 16% in Q2 to just 4% in Q3, which they attribute to people becoming more accustomed to this crisis. Additionally, social engineering attacks targeting organizations fell from 67% of all attempts in Q1 to under half (45%) in Q3.
https://www.infosecurity-magazine.com/news/ransomware-attacks-surge-q3/
In 2021, there will be a cyber attack every 11 seconds. Here’s how to protect yourself
Experienced outdoor athletes know that with winter rapidly approaching, the secret to success lies in protecting the core. That is, the body’s core temperature through layering, wicking and a host of ever-improving technical fabrics that prevent the cold, snow and ice from affecting performance. The same could be said for cyber security. With organizations and workers now in their ninth month of COVID-19, the time has come to prepare as the threat of cyber attacks becomes even more menacing.
The US, and much of the West, has suffered a massive cyber breach. It's hard to overstate how bad it is
Recent news articles have all been talking about the massive Russian cyber-attack against the United States, but that’s wrong on two accounts. It wasn’t a cyber-attack in international relations terms, it was espionage. And the victim wasn’t just the US, it was the entire world. But it was massive, and it is dangerous.
Espionage is internationally allowed in peacetime. The problem is that both espionage and cyber-attacks require the same computer and network intrusions, and the difference is only a few keystrokes. And since this Russian operation isn’t at all targeted, the entire world is at risk – and not just from Russia. Many countries carry out these sorts of operations, none more extensively than the US. The solution is to prioritize security and defense over espionage and attack.
https://www.theguardian.com/commentisfree/2020/dec/23/cyber-attack-us-security-protocols
Big tech companies including Intel, Nvidia, and Cisco were all infected during the SolarWinds hack
Last week, news broke that IT management company SolarWinds had been hacked, possibly by the Russian government, and the US Treasury, Commerce, State, Energy, and Homeland Security departments have been affected — two of which may have had emails stolen as a result of the hack. Other government agencies and many companies are investigating due to SolarWinds’ extensive client list. The Wall Street Journal is now reporting that some big tech companies have been infected, too.
Cisco, Intel, Nvidia, Belkin, and VMware have all had computers on their networks infected with the malware. There could be far more: SolarWinds had stated that “fewer than 18,000” companies were impacted, as if that number is supposed to be reassuring, and it even attempted to hide the list of clients who used the infected software. Today’s news takes some of SolarWinds’ big-name clients from “possibly affected’’ to “confirmed affected.”
https://www.theverge.com/2020/12/21/22194183/intel-nvidia-cisco-government-infected-solarwinds-hack
Researchers share the lists of victims of SolarWinds hack
Security experts started analyzing the DGA mechanism used by threat actors behind the SolarWinds hack to control the Sunburst/Solarigate backdoor and published the list of targeted organizations. Researchers from multiple cybersecurity firms published a list that contains major companies, including Cisco, Deloitte, Intel, Mediatek, and Nvidia. The researchers decoded the DGA algorithm used by the backdoor to assign a subdomain of the C2 for each of the compromised organizations.
https://securityaffairs.co/wordpress/112555/hacking/solarwinds-victims-lists.html
Threats
Ransomware
Ransomware: Attacks could be about to get even more dangerous and disruptive
IOT
New Critical Flaws in Treck TCP/IP Stack Affect Millions of IoT Devices
Malware
Emotet Returns to Hit 100K Mailboxes Per Day
Microsoft has discovered yet more SolarWinds malware
3 million users hit with infected Google Chrome and Microsoft Edge extensions
Vulnerabilities
Windows zero-day with bad patch gets new public exploit code
Script for detecting vulnerable TCP/IP stacks released
New SUPERNOVA backdoor found in SolarWinds cyberattack analysis
Smart Doorbell Disaster: Many Brands Vulnerable to Attack
Zero-day exploit used to hack iPhones of Al Jazeera employees
Signal: Cellebrite claimed to have 'cracked' chat app's encryption
Data Breaches
There's been a Nintendo Switch data leak, according to reports
Data breach hits 30,000 signed up to workplace pensions provider
Thousands of customer records exposed after serious data breach
Organised Crime
Cyber criminals have started indexing the dark web
Joker’s Stash Carding Site Taken Down
International sting shuts down 'favourite' VPN of cyber criminals
Dark Web Pricing Skyrockets for Microsoft RDP Servers, Payment-Card Data
NSA Warns of Hacking Tactics That Target Cloud Resources
Denial of Service
Cloudflare has identified a new type of DDoS attack inspired by an acoustic beat
Privacy
The pandemic has taken surveillance of workers to the next level
Other News
Dozens of Al Jazeera journalists allegedly hacked using Israeli firm's spyware
As usual, contact us to help assess where your risks lie and to ensure you are doing all you can do to keep you and your business secure.
Look out for our weekly ‘Cyber Tip Tuesday’ video blog and on our YouTube channel.
You can also follow us on Facebook, Twitter and LinkedIn.
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
Cyber Briefing 23 October 2020: Ransomware Continues to Evolve; Infected IoT Up 100%; Brute Force Attacks Up with more Open RDP Ports; 40% Unsure on Mobile Phishing; Most Imitated Phishing Brands
Cyber Briefing 23 October 2020: Ransomware Variants Evolve as Crooks Chase Bigger Paydays; Infected IoT Surges 100% in a Year; Brute Force Attacks Up Due To More Open RDP Ports; 40% of Users Not Sure What Mobile Phishing Is; Microsoft Most Imitated Phishing Brand Q3 2020; DDoS Triples as Ransoms Re-Emerge; Exploited Chrome Bug Fixed; WordPress Forces Security Update; The Most Worrying Vulns Around Today
Welcome to this week’s Black Arrow Cyber Threat Briefing – a weekly digest, collated and curated by our cyber experts to provide senior and middle management with an easy to digest round up of the most notable threats, vulnerabilities and cyber related news from the last week.
Threats
Ransomware
This week has been busy with ransomware related news, including new charges against Russian state-sponsored hackers and numerous attacks against well-known organisations.
In 2017, there was an attack utilizing the NotPetya ransomware to destroy data on systems worldwide. This week, the US govt indicted six Russian intelligence operatives [source], known to be part of the notorious 'Sandworm' group, for hacking operations, including NotPetya.
Ransomware variants continue to evolve as crooks chase bigger paydays
The number of ransomware attacks which threaten to leak stolen data if the victim doesn't pay a ransom to get their encrypted files and servers back is growing – and this is being reflected in the changing nature of the cyber criminal market.
Analysis by cyber security researchers found that over the last three months – between July and September - 80 percent of ransomware attacks combined with data dumps were associated with four families of ransomware – Maze, Sodinokibi, Conti and Netwalker.
The period from April to June saw just three ransomware families account for 80 percent of alerts – DoppelPaymer, Maze and Sodinokibi.
The way DoppelPayer has dropped off and how Conti and NetWalker have suddenly emerged some of the most prolific threats shows how the ransomware space continues to evolve, partly because of how successful it has already become for the crooks behind it. [source]
Why this matters:
Maze was the first major family of ransomware to add threats of data breaches to their ransom demands and other ransomware operators have taken note – and stolen the additional extortion tactic.
There is an inherent competitive nature that has befallen the ransomware landscape. The saturated ransomware market pushes ransomware developers to cut through the noise and gain the best ransomware title and this drives more affiliates to carry out their work and, thus, more successful attacks to reach their goal: to make as much money as possible.
DoppelPaymer's activity has dropped over the last few months – although it still remains active - enabling Conti and NetWalker to grab a larger slice of the pie.
Notable ransomware victims of the last week
French IT giant Sopra Steria hit by Ryuk ransomware
French IT services giant Sopra Steria suffered a cyber attack on October 20th, 2020, that reportedly encrypted portions of their network with the Ryuk ransomware.
Sopra Steria is a European information technology company with 46,000 employees in 25 countries worldwide. The company provides a wide range of IT services, including consulting, systems integration, and software development.
The firm has said that the attack has hit all geographies where they operate and have said it will take them several weeks to recover.
Numerous sources have confirmed that it was Ryuk ransomware threat actors who were behind the attack. This hacking group is known for its TrickBot and BazarLoader infections that allow threat actors to access a compromised network and deploy the Ryuk or Conti ransomware infections.
BazarLoader is increasingly being used in Ryuk attacks against high-value targets due to its stealthy nature and is less detected than TrickBot by security software.
When installed, BazarLoader will allow threat actors to remotely access the victim's computer and use it to compromise the rest of the network.
After gaining access to a Windows domain controller, the attackers then deploy the Ryuk ransomware on the network to encrypt all of its devices, as illustrated in the diagram above. [Source1] [source2]
The Nefilim ransomware operators have posted a long list of files that appear to belong to Italian eyewear and eyecare giant Luxottica.
Luxottica Group S.p.A. is an Italian eyewear conglomerate and the world’s largest company in the eyewear industry (which owns brands including LensCrafters, Sunglass Hut, Apex by Sunglass Hut, Pearle Vision, Target Optical, Eyemed vision care plan, and Glasses.com. Its best known brands are Ray-Ban, Persol, and Oakley) and employs over 80,000 people and generated 9.4 billion in revenue for 2019.
The company was hit by a cyber attack and some of the web sites operated by the company were not reachable, including Ray-Ban, Sunglass Hut, LensCrafters, EyeMed, and Pearle Vision.
Reports indicate that the firm was using a Citrix ADX controller device vulnerable to a critical vulnerability and it is believed that a threat actor or actors exploited the above flaw to infect the systems at the company with ransomware. This appears to have subsequently confirmed with Nefilim ransomware operators having posted a long list of files that appear to belong to Luxottica. [source]
Why this matters:
The analysis of the leaked files revealed that they contain confidential information regarding the recruitment process, professional resumes, and info about the internal structures of the Group’s human resource department. The ransomware operators also published a message which accuses Luxottica of having failed the properly manage the attack.
In the past months, the number of ransomware attacks surged, numerous ransomware gangs made the headlines targeting organisations worldwide and threatening victims with releasing the stolen data if the ransom was not paid.
Extortion is the new thing in cyber crime right now, more so than in the past. Companies cannot hide the cyber attack anymore. Now it’s more about how to manage the breach from the communication perspective. Defending companies from these types of attacks becomes even more strategic: data leak damages can generate tremendous amount of costs for companies worldwide.
Other notable ransomware victims this week include:
Barnes & Noble hit by Egregor ransomware, strange data leaked [source]
Montreal's STM public transport system hit by ransomware attack [source]
WastedLocker ransomware hits US-based ski and golf resort operator Boyne Resorts (WastedLocker was the same one used in the attack on Garmin in July) [source]
Other Threats
Infected IoT Device Numbers Surge 100% in a Year
The volume of infected Internet of Things (IoT) devices globally has soared by 100% over the past year, according to new data from Nokia.
It revealed that infected IoT devices now comprise nearly a third (32.7%) of the total number of devices, up from 16.2% in the 2019 report.
Nokia argued that infection rates for connected devices depend dramatically upon the visibility of the devices on the internet.
In networks where devices are routinely assigned public facing internet IP addresses there is a higher infection rate. In networks where carrier grade NAT is used, the infection rate is considerably reduced, because the vulnerable devices are not visible to network scanning.
With the introduction of 5G well underway, it is expected that not only the number of IoT devices will increase dramatically, but also the share of IoT devices accessible directly from the internet will increase as well, and rates of infection rising accordingly. [source]
Brute force attacks increase due to more open RDP ports
While leaving your back door open while you are working from home may be something you do without giving it a second thought, having unnecessary ports open on your computer or on your corporate network is a security risk that is sometimes underestimated. That’s because an open port can be subject to brute force attacks.
A brute force attack is where an attacker tries every way he can think of to get in. Including throwing the kitchen sink at it. In cases where the method they are trying is to get logged in to your system, they will try endless combinations of usernames and passwords until a combination works.
Brute force attacks are usually automated, so it doesn’t cost the attacker a lot of time or energy. Certainly not as much as individually trying to figure out how to access a remote system. Based on a port number or another system specific property, the attacker picks the target and the method and then sets his brute force application in motion. He can then move on to the next target and will get notified when one of the systems has swallowed the hook.
RDP attacks are one of the main entry points when it comes to targeted ransomware operations. To increase effectiveness, ransomware attacks are getting more targeted and one of the primary attack vectors is the Remote Desktop Protocol (RDP). Remote desktop is exactly what the name implies, an option to remotely control a computer system. It almost feels as if you were actually sitting behind that computer. Which is exactly what makes an attacker with RDP access so dangerous. [source]
Why this matters:
Because of the current pandemic, many people are working from home and may be doing so for a while to come. Working from home has the side effect of more RDP ports being opened. Not only to enable the workforce to access company resources from home, but also to enable IT staff to troubleshoot problems on the workers’ devices. A lot of enterprises rely on tech support teams using RDP to troubleshoot problems on employee’s systems.
But ransomware, although prevalent, is not the only reason for these types of attacks. Cyber criminals can also install keyloggers or other spyware on target systems to learn more about the organization they have breached. Other possible objectives might be data theft, espionage, or extortion.
Phishing
Two in five employees are not sure what a mobile phishing attack is
The COVID-19 pandemic has clearly changed the way people work and accelerated the already growing remote work trend. This has also created new security challenges for IT departments, as employees increasingly use their own personal devices to access corporate data and services.
These changes, where employees, IT infrastructures, and customers are everywhere – has led to employees not prioritising security in their new world of work, and the current distributed remote work environment has also triggered a new threat landscape, with malicious actors increasingly targeting mobile devices with phishing attacks.
A new study looking at the impact that lockdown has had on employees working habits polled 1,200 workers across the US, UK, France, Germany, Belgium, Netherlands, Australia, and New Zealand showed that many employees were unaware of how to identify and avoid a phishing attack, and over two in five (43%) of employees are not even sure what a phishing attack is. [source]
Microsoft is Most Imitated Brand for Phishing Attempts in Q3 2020
The latest Check Point ‘Q3 Brand Phishing Report’, highlighting the brands that hackers imitated the most to lure people into giving up personal data, reveals the brands which were most frequently imitated by criminals in their attempts to steal individuals’ personal information or payment credentials during July, August and September.
In Q3, Microsoft was the most frequently targeted brand by cyber criminals, soaring from fifth place (relating to 7% of all brand phishing attempted globally in Q2 of 2020) to the top of the ranking. 19% of all brand phishing attempts related to the technology giant, as threat actors sought to capitalise on large numbers of employees still working remotely during the Covid-19 pandemic. For the first time in 2020, DHL entered the top 10 rankings, taking the second spot with 9% of all phishing attempts related to the company. [source]
Top phishing brands in Q3 2020
Microsoft (19%)
DHL (9%)
Google (9%)
PayPal (6%)
Netflix (6%)
Facebook (5%)
Apple (5%)
Whatsapp (5%)
Amazon (4%)
Instagram (4%)
Phishing Lures Shifting from COVID-19 updates to Job Opportunities
Researchers are seeing a pivot in the spear-phishing and phishing lures used by cybercriminals, to entice potential job candidates as businesses start to open up following the pandemic.
Cyber criminals cashed in on the surge of COVID-19 earlier this year, with email lures purporting to be from healthcare professionals offering more information about the pandemic. However, as the year moves forward, bad actors are continuing to swap up their attacks and researchers are now seeing ongoing email based attacks that tap into new job opportunities as businesses start to open up. [source]
Denial of Service Attacks
DDoS (Distributed Denial of Service) Attacks Triple in Size as Ransom Demands Re-Emerge
The last quarter of 2020 has seen a wave of web application attacks which have used ransom letters to target businesses across a number of industries.
According to research from Akamai, the largest of these attacks sent over 200Gbps of traffic at their targets as part of a sustained campaign of higher Bits Per Second (BPS) and Packets Per Second (PPS) than similar attacks had displayed a few weeks prior.
Prior to August most of these attacks were targeting the gaming industry but since then these attacks abruptly swung to financial organisations, and later in the cycle, multiple other verticals.
Akamai explained that none of the vectors involved in these series of attacks were new, as most of the traffic was generated by reflectors and systems that were used to amplify traffic. However, multiple organisations began to receive targeted emails with threats of DDoS attacks, where this would be launched unless a ransom amount was paid. A small DDoS would be made against the company to show that the attackers were serious, and then there was a threat of a 1Tbps attack if payment was not made.
Many extortion DDoS campaigns start as a threat letter, and never progress beyond that point but this this campaign has seen frequent ‘sample’ attacks that prove to the target that criminals have the capability to make life difficult.
Many of the extortion emails ended up being caught by spam filters, and not all targets are willing to admit they’ve received an email from the attackers.
Why this matters:
This extortion DDoS campaign is not over and the criminals behind this campaign are changing and evolving their attacks in order to throw off defenders and the law enforcement agencies that are working to track them down.
Vulnerabilities
New Google Chrome version fixes actively exploited zero-day bug
Google released Chrome 86.0.4240.111 this week to address five security vulnerabilities, one of which is being actively exploited.
The announcement from Google stated they they were aware of reports that an exploit for CVE-2020-15999 exists in the wild.
This new version of Chrome started rolling out to the entire userbase. Users on Windows, Mac, and Linux desktop users can upgrade to Chrome 86 by going to Settings -> Help -> About Google Chrome.
The Google Chrome web browser will then automatically check for the new update and install it when available.
Adobe releases another out-of-band patch, squashing critical bugs across creative software
Adobe has released a second out-of-band security update to patch critical vulnerabilities across numerous software products.
The patch, released outside of the tech giant's typical monthly security cycle, impacts Adobe Illustrator, Dreamweaver, Marketo, Animate, After Effects, Photoshop, Premiere Pro, Media Encoder, InDesign, and the Creative Cloud desktop application on Windows and macOS machines.
The vulnerabilities across the different products variously could result in privilege escalation, cross-site scripting (XSS), which could be weaponised to deploy malicious JavaScript in a browser session, or otherwise could result in arbitrary code execution.
Last week, Adobe released a separate set of out-of-band security fixes impacting the Magento platform. On October 15, Adobe said the patch resolved nine vulnerabilities, eight of which are critical -- including a bug that could be abused to tamper with Magento customer lists. [source]
WordPress deploys forced security update for dangerous bug in popular plugin
The WordPress security team has taken a rare step last week and used a lesser-known internal capability to forcibly push a security update for a popular plugin called Loginizer, which provides security enhancements for the WordPress login page, but that was found to contain a dangerous SQL injection bug that could have allowed hackers to take over WordPress sites running older versions of the plugin. [source]
Why this matters:
Remote attackers to run code against the WordPress database — in what is referred to as an unauthenticated SQL injection attack.
These are the most worrying vulnerabilities around today
Failure to patch once again leaves organisations open to attacks
The US National Security Agency (NSA) has published a new cyber security advisory in which it details 25 of the most dangerous vulnerabilities actively being exploited in the wild by Chinese state-sponsored hackers and other cyber criminals.
Unlike zero-day vulnerabilities where hardware and software makers have yet to release a patch, all of the vulnerabilities in the NSA's advisory are well-known and patches have been made available to download from their vendors. However, the problem lies in the fact that organisations have yet to patch their systems, leaving them vulnerable to potential exploits and attacks.
The NSA provided further details on the nature of the vulnerabilities in its advisory while urging organisations to patch them immediately.
Most of the vulnerabilities listed below can be exploited to gain initial access to victim networks using products that are directly accessible from the Internet and act as gateways to internal networks. The majority of the products are either for remote access or for external web services and should be prioritised for immediate patching. The full list can be found here.
The first bug in the list, tracked as CVE-2019-11510, relates to Pulse Secure VPN servers and how an unauthenticated remote attacker can expose keys or passwords by sending a specially crafted URI to perform an arbitrary file reading vulnerability.
Another notable bug from the list, tracked as CVE-2020-5902, affects the Traffic Management User Interface (TMUI) of F5 BIG-IP proxies and load balancers and it is vulnerable to a Remote Code Execution (RCE) vulnerability that if exploited, could allow a remote attacker to take over an entire BIG-IP device.
The Citrix Application Delivery Controller (ADC) and Gateway systems are vulnerable to a directory traversal bug, tracked as CVE-2019-19781, that can lead to remote code execution where an attacker does not need to possess valid credentials for the device.
The advisory also mentions BlueKeep, SigRed, Netlogon, CurveBall and other more well-known vulnerabilities.
To avoid falling victim to any potential attacks exploiting these vulnerabilities, the NSA recommends that organisations keep their systems and products updated and patched as soon as possible after vendors release them. [source]
Miscellaneous Cyber News of the Weeks
Hackers Can Clone Millions of Toyota, Hyundai, and Kia Keys
Owners of cars with keyless start systems have learned to worry about so-called relay attacks, in which hackers exploit radio-enabled keys to steal vehicles without leaving a trace. Now it turns out that many millions of other cars that use chip-enabled mechanical keys are also vulnerable to high-tech theft. A few cryptographic flaws combined with a little old-fashioned hot-wiring—or even a well-placed screwdriver—lets hackers clone those keys and drive away in seconds.
Researchers this week revealed new vulnerabilities in the encryption systems used by immobilisers, the radio-enabled devices inside of cars that communicate at close range with a key fob to unlock the car's ignition and allow it to start. Specifically, they found problems in how Toyota, Hyundai, and Kia implement their encryption system. A hacker who swipes a relatively inexpensive RFID reader/transmitter device near the key fob of any affected car can gain enough information to derive its secret cryptographic value. That, in turn, would allow the attacker to spoof the device to impersonate the key inside the car, disabling the immobiliser and letting them start the engine.
The researchers say the affected car models include the Toyota Camry, Corolla, and RAV4; the Kia Optima, Soul, and Rio; and the Hyundai I10, I20, and I40, amongst others. [source]
As usual, contact us to help assess where your risks lie and to ensure you are doing all you can do to keep you and your business secure.
Look out for our weekly ‘Cyber Tip Tuesday’ video blog and on our YouTube channel.
You can also follow us on Facebook, Twitter and LinkedIn.
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
Cyber Threat Briefing 16 October 2020: ransomware tidal wave; notable ransomware victims from the last week; BEC Attacks: Nigeria no longer epicentre, losses top $26B; Trickbot back; MS fix 87 vulns
Cyber Threat Briefing 16 October 2020: ransomware tidal wave of attacks; Notable ransomware victims of the last week; BEC Attacks: Nigeria No Longer the Epicentre as Losses top $26B; Trickbot back after disruption attempts; Microsoft October 2020 Patch Tuesday fixes 87 vulnerabilities; Malware gangs love open source offensive hacking tools
Welcome to this week’s Black Arrow Cyber Threat Briefing – a weekly digest, collated and curated by our cyber experts to provide senior and middle management with an easy to digest round up of the most notable threats, vulnerabilities and cyber related news from the last week.
Threats
Ransomware
Ransomware is growing and growing and getting worse all the time, with the G7 this week warning of ‘a tidal wave of ransomware attacks’ [source]. It is fast approaching becoming such a problem that it may soon reach epidemic status with few organisations left unaffected as firm after firm falls victim.
The ransomware gangs have turned crime into a multi-million pound business empire, it is estimated that $7.5 billion was extorted from victims last year in the United States alone [source], putting any legitimate industry or business sector to shame in term of meteoric growth. This is not small scale actors working out of their bedrooms, they have customer support centres and 24/7 helplines, they have plush offices and flash cars, paid for by the victims of their crimes, paid for by firms like yours paying ransoms.
And here's how attackers are getting in: in nearly half (47%) of ransomware cases gangs used the open remote desktop protocol, a tool that has been used by many companies to help staff work from home, but which can also give attackers a way in if it is not correctly secured.
More than a quarter (26%) of cases were traced back to a phishing email, and a smaller number used specific vulnerability exploits (17%), including Citrix NetScaler CVE-2019-19781 and Pulse VPN CVE-2019-11510. This was followed by account takeovers, at 10%. [source]
Criminal gangs have earned so much money and power they are now outsourcing much of the labour, allowing them to live of their spoils while their empires continue to grow, while they do next to nothing, with more and more joining their ranks [source]
As long as even a small number of victims pay the ransom this remains highly lucrative for attackers.
The ransom for Software AG is $23m, but they will demand much smaller sums from much smaller firms – so how are they doing this? Are larger firms being specifically targeted with tailored phishing campaigns, where they hope they will get lucky in getting an employee to fall for the bait, where lower value targets are being hit with machine/algorithmic generated phishing attacks, with lower levels of sophistication and more of a ‘spray and pray’ approach, hoping casting a wide enough net will still result in larger numbers of lower value victims.
We keep trying to warn firms how bad this is getting, and we don’t do this to drum up business, we do this because we are hugely concerned about the direction this is going and how damaging this can be for any firm.
Many firms are reluctant to take cyber security seriously, believing it won’t happen to them, but it is happening to firm after firm after firm who believed it wouldn’t happen to them. It’s too late to start thinking about what you should have done after you’ve become a victim, it’s far better, and far cheaper, to take steps to avoid being a victim in the first place than trying to recover or pay the ransom.
Of the increasing number of firms that do go hit, many don’t survive, and those that do often find things are never the same again, with impacts on confidence levels in your staff and in your IT and information security departments [source]
Ransomware is not only affecting desktops, laptops and servers, but also now increasingly Android and other mobile platforms [source]
Protecting against ransomware is not a luxury or something that can kicked down the road to look at another day, firms need to ensure they are protecting themselves against this threat now – before they become a victim.
Notable ransomware victims of the last week
There have been a number of high profile victims of ransomware in the last week, notably Software AG, a German conglomerate with operations in more than 70 countries, which was attacked by the Clop group who are threatening to dump stolen data if the $23 million ransom is not paid.
Carnival Cruises were hit with ransomware affecting data and personal information for guests, employees and crew for Carnival Cruises, Holland America and Seabourn as well as casino operations.
Early indications point to the disruption being experiences by Hackney Council with their systems stemming from a ransomware attack, although this has not been confirmed.
BEC
BEC Attacks: Nigeria No Longer the Epicentre as Losses top $26B
Business Email Compromise (BEC) Fraudsters now have bases of operation across at least 39 countries and are responsible for $26 billion in losses annually, and growing.
A study of more than 9,000 instances of BEC attacks all over the world shows that the number has skyrocketed over the past year, and that the social-engineering scam has expanded well beyond its historic roots in Nigeria.
Why this matters:
A recent report entitled The Global Reach of Business Email Compromise, found that these attacks cost businesses a staggering $26 billion every year. And that trend appears to be accelerating. In fact, researchers found BEC attacks currently make up a full 40 percent of cyber crime losses globally, impacting at least 177 countries.
For context, the Anti-Phishing Working Group recently find that the average wire transfer in a BEC scan is around $80,000.
In a BEC attack, a scammer impersonates a company executive or other trusted party and tries to trick an employee responsible for payments or other financial transactions into writing money to a bogus account. Attackers usually conduct a fair amount of recon work, studying executive styles and uncovering the organisations vendors, billing system practices and other information to help mount a convincing attack.
Read more: https://threatpost.com/bec-attacks-nigeria-losses-snowball/160118/
Trickbot back after disruption attempts
The Trickbot botnet looks to be working once again, despite separate efforts in the past few weeks aimed at disrupting its operation.
Earlier this month the Emotet spam botnet – which is often the precursor to TrickBot being loaded onto a system – began receiving spam templates intended for mass distribution. These spam templates contained Microsoft Word document attachments with malicious macros that fetch and load a copy of Emotet onto the victim machine. The Emotet bot reached out to its controllers and received commands to download and execute Trickbot on victim machines.
The Trickbot group tag that researchers identified is tied to a typical infection campaign that information security researchers have been observing for the past 6 months or more.
Additionally, Intel 471 researchers saw an update to the Trickbot plugin server configuration file. Fifteen server addresses were added, and two old servers were retained in the configuration, along with the server’s ‘.onion’ address. This was likely done as a fix that would help operators maintain that their infrastructure remains operational. [link]
Why this matters:
The fix is another round in the back-and-forth between Trickbot’s operators and the separate public and private sector parties that have attempted to disrupt the botnet’s actions. This includes actions by the US Cyber Command and Microsoft, who issued a public statement that it had taken legal action to “combat ransomware ahead of U.S. elections.” The legal action involved Microsoft attempting to disrupt a number of Trickbot command and control server IP addresses in the United States.
The fact that Trickbot has resumed normal operations despite the best efforts of the likes of the US Cyber Command and Microsoft shows how resilient of an operation Trickbot is, and how much more effort is needed to fully take the botnet offline for good. The botnet’s operators have all the IT support of legitimate enterprises – continuity planning, backups, automated deployment, and a dedicated workforce – that allow them to quickly react to disruptive measures.
Read more: https://public.intel471.com/blog/trickbot-online-emotet-microsoft-cyber-command-disruption-attempts/
Vulnerabilities
Microsoft October 2020 Patch Tuesday fixes 87 vulnerabilities
Microsoft this week released its monthly batch of security updates known as Patch Tuesday, and this month the OS maker has patched 87 vulnerabilities across a wide range Microsoft products.
By far, the most dangerous bug patched this month is CVE-2020-16898. Described as a remote code execution (RCE) vulnerability in the Windows TCP/IP stack, this bug can allow attackers to take over Windows systems by sending malicious ICMPv6 Router Advertisement packets to an unpatched computer via a network connection.
Another bug to keep an eye on is CVE-2020-16947, a remote code execution issue in Outlook. Microsoft says this bug can be exploited by tricking a user to open a specially crafted file with an affected version of Microsoft Outlook software. [source1] [source2]
Why this matters:
The bug was discovered internally by Microsoft engineers, and OS versions vulnerable to CVE-2020-16898 include Windows 10 and Windows Server 2019.
With a severity score of 9.8 out of a maximum 10, Microsoft considers the bug dangerous and likely to be weaponised, and rightfully so.
Patching the bug is recommended, but workarounds such as disabling ICMPv6 RDNSS support also exist, which would allow system administrators to deploy temporary mitigations until they quality-test this month’s security updates for any OS-crashing bugs.
Critical SonicWall VPN Portal Bug Allows DoS, Worming RCE
A critical security bug in the SonicWall VPN Portal can be used to crash the device and prevent users from connecting to corporate resources. It could also open the door to remote code execution (RCE), researchers said.
The flaw (CVE-2020-5135) is a stack-based buffer overflow in the SonicWall Network Security Applicance (NSA). According to researchers who discovered it, the flaw exists within HTTP/HTTPS service used for product management and SSL VPN remote access. [source]
Why this matters:
An unskilled attacker could trigger a persistent denial-of-service condition using an unauthenticated HTTP request involving a custom protocol handler.
Adding insult to injury, this particular flaw exists in a pre-authentication routine, and within a component (SSL VPN) which is typically exposed to the public internet.
‘More Than A Billion’ Phone Wide Open To ‘Backdoor’ Remote Code Execution in Adtech Company’s Code
Malicious code impacting more than a billion smartphone owners is currently in the wild and enabling remote code execution. [source]
Why this matters:
Remote code execution is a very serious security violation, and basically enables the owner of that code do almost anything they want on your phone.
Miscellaneous Cyber News of the Weeks
Malware gangs love open source offensive hacking tools
In the cyber security field, the term OST (Open Source Tools) refers to software apps, libraries, and exploits that possess offensive hacking capabilities and have been released as either free downloads or under an open source license.
OST projects are usually released to provide a proof-of-concept exploit for a new vulnerability, to demonstrate a new (or old) hacking technique, or as penetration testing utilities shared with the community.
These discussions have been taking place for more than a decade. However, they have always been based on personal experiences and convictions, and never on actual raw data.
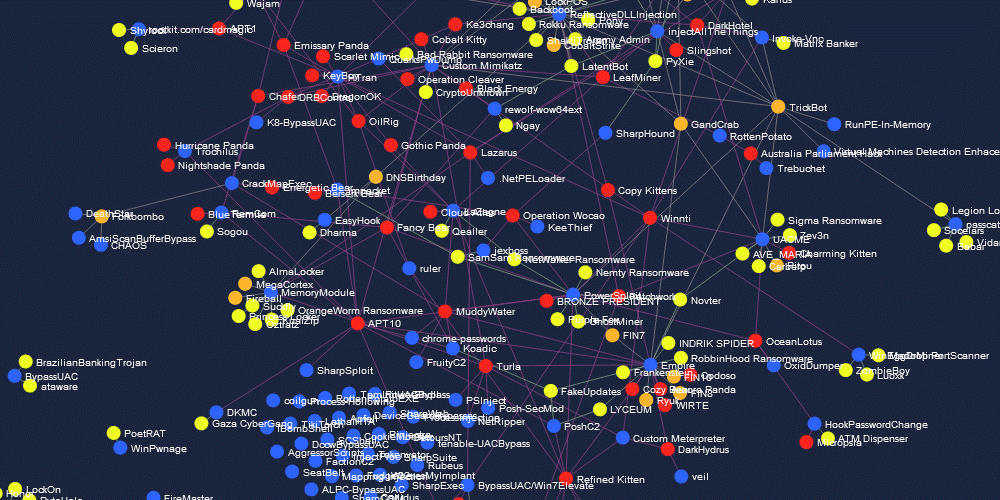
That changed this week when a security researcher compiled data on 129 open source offensive hacking tools and searched through malware samples and cyber-security reports to discover how widespread was the adoption of OST projects among hacking groups — such as low-level malware gangs, elite financial crime groups, and even nation-state sponsored APTs. [source]
The results were compiled in an interactive map – available here
Why this matters:
Today, OST is one of the most (if not the most) controversial topics in the information security community.
On one side, you have the people who are in favour of releasing such tools, arguing that they can help defenders learn and prepare systems and networks for future attacks.
On the opposing side, you have the ones who say that OST projects help attackers reduce the costs of developing their own tools and hiding activities into a cloud of tests and legitimate pen-tests.
Fitbit Spyware Steals Personal Data via Watch Face
A researcher has found they can take advantage of lax Fitbit privacy controls to build a malicious spyware watch face.
A wide-open app-building API (Application Programming Interface) could allow an attacker to build a malicious application that could access Fitbit user data, and send it to any server.
A proof-of-concept was created to do just that, after realizing that Fitbit devices are loaded with sensitive personal data. [source]
Why this matters:
Essentially, the API could send device type, location and user information including gender, age, height, heart rate and weight and it could also access calendar information. While this doesn’t include PII profile data, the calendar invites could expose additional information such as names and locations.
The researcher was able to make the app available through the Fitbit Gallery (where Fitbit showcases various third-party and in-house apps). Thus, the spyware appears legitimate, and increase the likelihood it would be downloaded.
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
As usual, contact us to help assess where your risks lie and to ensure you are doing all you can do to keep you and your business secure.
Look out for our weekly ‘Cyber Tip Tuesday’ video blog and on our YouTube channel.