Threat Intelligence Blog

Contact us to discuss any insights from our Blog, and how we can support you in a tailored threat intelligence report.
Black Arrow Cyber Threat Briefing 04 December 2020
Black Arrow Cyber Threat Briefing 4 December 2020: Covid vaccine supply chain targeted by hackers; Criminals Favour Ransomware and BEC; Bank Employee Sells Personal Data of 200,000 Clients; 2020 Pandemic changing short- and long-term approaches to risk; Cyber risks take the fun out of connected toys; Remote Workers Admit Lack of Security Training
Welcome to this week’s Black Arrow Cyber Threat Briefing – a weekly digest, collated and curated by our cyber experts to provide senior and middle management with an easy to digest round up of the most notable threats, vulnerabilities and cyber related news from the last week.
Top Cyber Headlines of the Week
Covid vaccine supply chain targeted by hackers, say security experts
Cyber attackers have targeted the cold supply chain needed to deliver Covid-19 vaccines, according to a report detailing a sophisticated operation likely backed by a nation state.
The hackers appeared to be trying to disrupt or steal information about the vital processes to keep vaccines cold as they travel from factories to hospitals and doctors’ offices.
https://www.ft.com/content/9c303207-8f4a-42b7-b0e4-cf421f036b2f
Criminals to Favour Ransomware and BEC Over Breaches in 2021
The era of the mega-breach may be coming to an end as cyber-criminals eschew consumers’ personal data and focus on phishing and ransomware.
Cyber-criminals are relying less on stolen personal information and more on “poor consumer behaviors” such as password reuse to monetize attacks.
https://www.infosecurity-magazine.com/news/criminals-favor-ransomware-bec/
Bank Employee Sells Personal Data of 200,000 Clients
South Africa–based financial services group Absa has stated that one of its employees sold the personal information of 200,000 clients to third parties.
The group confirmed on Wednesday that the illegal activity had occurred and that 2% of Absa's retail customer base had been impacted.
The employee allegedly responsible for it was a credit analyst who had access to the group's risk-modeling processes.
Data exposed as a result of the security incident included clients' ID numbers, addresses, contact details, and descriptions of vehicles that they had purchased on finance.
https://www.infosecurity-magazine.com/news/bank-employee-sells-personal-data/
LastPass review: Still the leading password manager, despite security history
"'Don't put all your eggs in one basket' is all wrong. I tell you 'put all your eggs in one basket, and then watch that basket,'" said industrialist Andrew Carnegie in 1885. When it comes to privacy tools, he's usually dead wrong. In the case of password managers, however, Carnegie is usually more dead than wrong. To wit, I have been using LastPass so long I don't know when I started using LastPass and, for now, I've got no reason to change that.
The most significant security innovations of 2020
Who gets access? That is the question that drives every security measure and innovation that’s landed on PopSci’s annual compendium since we launched the category in 2008. Every year, that question gets bigger and bigger. In 2020, the world quaked under a global pandemic that took 1.4 million lives, the US saw a rebirth in its civil rights movement, and a spate of record-breaking wildfires forced entire regions to evacuate. And those are just the new scares. A buildup of angst against ad trackers and app snooping led to major changes in hardware and software alike. It was a year full of lessons, nuances, and mini revolutions, and we strive to match that with our choices.
https://www.popsci.com/story/technology/most-important-security-innovations-2020/
2020 security priorities: Pandemic changing short- and long-term approaches to risk
Security planning and budgeting is always an adventure. You can assess current risk and project the most likely threats, but the only real constant in cybersecurity risk is its unpredictability. Layer a global pandemic on top of that and CISOs suddenly have the nearly impossible task of deciding where to request and allocate resources in 2021.
Show how the COVID pandemic has changed what security focuses on now and what will drive security priorities and spending in 2021. Based on a survey of 522 security professionals from the US, Asia/Pacific and Europe, the study reveals how the pandemic has changed the way organizations assess risk and respond to threats—permanently.
Cyber risks take the fun out of connected toys
As Christmas approaches, internet-enabled smart toys are likely to feature heavily under festive trees. While some dolls of decades past were only capable of speaking pre-recorded phrases, modern equivalents boast speech recognition and can search for answers online in real time.
Other connected gadgets include drones or cars such as Nintendo’s Mario Kart Live Home Circuit, where players race each other in a virtual world modelled after their home surroundings.
But for all the fun that such items can bring, there is a risk — poorly-secured Internet of Things toys can be turned into convenient tools for hackers.
https://www.ft.com/content/c653e977-435f-4553-8401-9fa9b0faf632
Remote Workers Admit Lack of Security Training
A third of remote working employees have not received security training in the last six months.
400 remote workers in the UK across multiple industries, while 83% have had access to security best practice training and 88% are familiar with IT security policies, 32% have received no security training in the last six months.
Also, 50% spend two or more hours a week on IT issues, and 42% felt they had to go around the security policies of their organization to do their job.
https://www.infosecurity-magazine.com/news/remote-workers-training/
Threats
Ransomware
Delaware County Pays $500,000 Ransom After Outages
A US county is in the process of paying half-a-million dollars to ransomware extorters who locked its local government network, according to reports.
Pennsylvania’s Delaware County revealed the attack last week, claiming in a notice that it had disrupted “portions of its computer network.
“We commenced an immediate investigation that included taking certain systems offline and working with computer forensic specialists to determine the nature and scope of the event. We are working diligently to restore the functionality of our systems,” it said.
https://www.infosecurity-magazine.com/news/delaware-county-pays-500k-ransom/
MasterChef Producer Hit by Double Extortion Ransomware
A multibillion-dollar TV production company has become the latest big corporate name caught out by ransomware, it emerged late last week.
The firm owns over 120 production firms around the world, delivering TV shows ranging from MasterChef and Big Brother to Black Mirror and The Island with Bear Grylls.
In a short update last Thursday, it claimed to be managing a “cyber-incident” affecting the networks of Endemol Shine Group and Endemol Shine International, Dutch firms it acquired in a $2.2bn deal in July.
Although ransomware isn’t named in the notice, previous reports suggest the firm is being extorted.
https://www.infosecurity-magazine.com/news/masterchef-producer-double/
Sopra Steria to take multi-million euro hit on ransomware attack
The company revealed in October that it had been hit by hackers using a new version of Ryuk ransomware.
It now says that the fallout, with various systems out of action, is likely to have a gross negative impact on operating margin of between €40 million and €50 million.
The group's insurance coverage for cyber risks is EUR30 million, meaning that negative organic revenue growth for the year is now expected to be between 4.5% and five per cent (previously between two per cent and four per cent). Free cash flow is now expected to be between €50 million and €100 million (previously between €80 million and €120 million).
BEC
FBI: BEC Scams Are Using Email Auto-Forwarding
The agency notes in an alert made public this week that since the COVID-19 pandemic began, leading to an increasingly remote workforce, BEC scammers have been taking advantage of the auto-forwarding feature within compromised email inboxes to trick employees to send them money under the guise of legitimate payments to third parties.
This tactic works because most organizations do not sync their web-based email client forwarding features with their desktop client counterparts. This limits the ability of system administrators to detect any suspicious activities and enables the fraudsters to send malicious emails from the compromised accounts without being detected, the alert, sent to organizations in November and made public this week, notes.
https://www.bankinfosecurity.com/fbi-bec-scams-are-using-email-auto-forwarding-a-15498
Phishing
Phishing lures employees with fake 'back to work' internal memos
Scammers are trying to steal email credentials from employees by impersonating their organization's human resources (HR) department in phishing emails camouflaged as internal 'back to work' company memos.
These phishing messages have managed to land in thousands of targeted individuals' mailboxes after bypassing G Suite email defences according to stats provided by researchers at email security company Abnormal Security who spotted this phishing campaign.
There is a high probability that some of the targets will fall for the scammers' tricks given that during this year's COVID-19 pandemic most companies have regularly emailed their employees with updates regarding remote working policy changes.
Warning: Massive Zoom phishing targets Thanksgiving meetings
Everyone should be on the lookout for a massive ongoing phishing attack today, pretending to be an invite for a Zoom meeting. Hosted on numerous landing pages, BleepingComputer has learned that thousands of users' credentials have already been stolen by the attack.
With many in the USA hosting virtual Thanksgiving dinners and people in other countries conducting Zoom business meetings, as usual, today is a prime opportunity to perform a phishing attack using Zoom invite lures.
Malware
All-new Windows 10 malware is excellent at evading detection
Security researchers at Kaspersky have discovered a new malware strain developed by the hacker-for-hire group DeathStalker that has been designed to avoid detection on Windows PCs.
While the threat actor has been active since at least 2012, DeathStalker first drew Kaspersky's attention back in 2018 because of its distinctive attack characteristics which didn't resemble those employed by cybercriminals or state-sponsored hackers.
https://www.techradar.com/news/all-new-windows-10-malware-is-excellent-at-evading-detection
New TrickBot version can tamper with UEFI/BIOS firmware
The operators of the TrickBot malware botnet have added a new capability that can allow them to interact with an infected computer's BIOS or UEFI firmware.
The new capability was spotted inside part of a new TrickBot module, first seen in the wild at the end of October, security firms Advanced Intelligence and Eclypsium said in a joint report published today.
The new module has security researchers worried as its features would allow the TrickBot malware to establish more persistent footholds on infected systems, footholds that could allow the malware to survive OS reinstalls.
https://www.zdnet.com/article/new-trickbot-version-can-tamper-with-uefibios-firmware/
Russia-linked APT Turla used a new malware toolset named Crutch
Russian-linked APT group Turla has used a previously undocumented malware toolset, named Crutch, in cyberespionage campaigns aimed at high-profile targets, including the Ministry of Foreign Affairs of a European Union country.
The Turla APT group (aka Snake, Uroburos, Waterbug, Venomous Bear and KRYPTON) has been active since at least 2007 targeting diplomatic and government organizations and private businesses in the Middle East, Asia, Europe, North and South America, and former Soviet bloc nations.
https://securityaffairs.co/wordpress/111813/apt/turla-crutch-malware-platform.html
MacBooks under attack by dangerous malware: What to do
a recent spate of malware attacks targeting macOS of late that installs backdoors to steal sensitive personal information. The security firm discovered that a new malware variant is being used online and backed by a rogue nation-state hacking group known as OceanLotus, which also operates under the name AKTP2 and is based in Vietnam.
The new malware was created by OceanLotus due to the “similarities in dynamic behavior and code” from previous malware connected to the Vietnamese-based hacking group.
https://www.laptopmag.com/news/macbooks-under-attack-by-dangerous-malware-what-to-do
Hackers Using Monero Mining Malware as Decoy, Warns Microsoft
The company’s intelligence team said a group called BISMUTH hit government targets in France and Vietnam with relatively conspicuous monero mining trojans this summer. Mining the crypto generated side cash for the group, but it also distracted victims from BISMUTH’s true campaign: credential theft.
Crypto-jacking “allowed BISMUTH to hide its more nefarious activities behind threats that may be perceived to be less alarming because they’re ‘commodity’ malware,” Microsoft concluded. It said the conspicuousness of monero mining fits BISMUTH’s “hide in plain sight” MO.
Microsoft recommended organizations stay vigilant against crypto-jacking as a possible decoy tactic.
https://www.coindesk.com/hackers-using-monero-mining-malware-as-decoy-warns-microsoft
Vulnerabilities
Zerologon is now detected by Microsoft Defender for Identity
There has been a huge focus on the recently patched CVE-2020-1472 Netlogon Elevation of Privilege vulnerability, widely known as ZeroLogon. While Microsoft strongly recommends that you deploy the latest security updates to your servers and devices, we also want to provide you with the best detection coverage possible for your domain controllers. Microsoft Defender for Identity along with other Microsoft 365 Defender solutions detect adversaries as they try to exploit this vulnerability against your domain controllers.
Privacy
'We've heard the feedback...' Microsoft 365 axes per-user productivity monitoring after privacy backlash
If you heard a strange noise coming from Redmond today, it was the sound of some rapid back-pedalling regarding the Productivity Score feature in its Microsoft 365 cloud platform.
Following outcry from subscribers and privacy campaigners, the Windows giant has now vowed to wind back the functionality so that it no longer produces scores for individual users, and instead just summarizes the output of a whole organization. It was feared the dashboard could have been used by bad bosses to measure the productivity of specific employees using daft metrics like the volume of emails or chat messages sent through Microsoft 365.
As usual, contact us to help assess where your risks lie and to ensure you are doing all you can do to keep you and your business secure.
Look out for our weekly ‘Cyber Tip Tuesday’ video blog and on our YouTube channel.
You can also follow us on Facebook, Twitter and LinkedIn.
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
Black Arrow Cyber Threat Briefing - 30 October 2020
Welcome to this week’s Black Arrow Cyber Threat Briefing – a weekly digest, collated and curated by our cyber experts to provide senior and middle management with an easy to digest round up of the most notable threats, vulnerabilities and cyber related news from the last week.
Threats
Ransomware
Furniture Giant Steelcase Hit by Suspected Ransomware Attack
Steelcase, the world’s largest maker of office furniture, revealed in a filing with the US Securities and Exchange Commission (SEC) that it had become the latest big name to be hit by a major ransomware attack.
The firm claimed to have detected a cyber-attack on its IT systems last Thursday, October 22.
“The company promptly implemented a series of containment measures to address this situation including temporarily shutting down the affected systems and related operations,” it continued. “The company is actively engaged in restoring the affected systems and returning to normal levels of operations.”
https://www.infosecurity-magazine.com/news/furniture-giant-steelcase/
Multinational energy company Enel Group hit by ransomware again, Netwalker demands $14 million
Multinational energy company Enel Group has been hit by a ransomware attack for the second time this year. This time by Netwalker, who is asking a $14 million ransom for the decryption key and to not release several terabytes of stolen data.
Enel is one of the largest players in the European energy sector, with more than 61 million customers in 40 countries. As of August 10, it ranks 87 in Fortune Global 500, with a revenue of almost $90 billion in 2019.
Ransomware vs WFH: How remote working is making cyber attacks easier to pull off
The unique conditions of 2020 mean businesses are more reliant on being digitally connected than ever before. Cyber criminals know this, which is why ransomware attacks have become even more pervasive – and effective during the course this year.Hackers are breaking into networks of organisations ranging from tech companies to local governments and almost every other sector; encrypting servers, services and files with ransomware before demanding a bitcoin ransom that can be measured in hundreds of thousands or even millions of dollars.
REvil ransomware gang claims over $100 million profit in a year
REvil ransomware developers say that they made more than $100 million in one year by extorting large businesses across the world from various sectors.
They are driven by profit and want to make $2 billion from their ransomware service, adopting the most lucrative trends in their pursuit of wealth.
Phishing
Remote Workers Ignore Training to Open Suspicious Emails
Remote workers are increasingly putting corporate data and systems at risk by failing to follow best practice security, according to new research from Mimecast.
The email security vendor polled over 1000 global respondents working from corporate machines to compile its latest report, Company-issued computers: What are employees really doing with them?
It found a litany of risky behaviour: for example, 73% of respondents frequently use their company-issued device for personal matters such as checking webmail (47%), carrying out financial transactions (38%) and online shopping (35%).
https://www.infosecurity-magazine.com/news/remote-workers-ignore-training/
Malware
Emotet campaign used parked domains to deliver malware payloads
Researchers tracking malicious use of parked domains have spotted the Emotet botnet using such domains to deliver malware payloads as part of a large scale phishing campaign.
Domain owners park their domains using parking service providers to monetize them via advertisement networks while they're not being used to host an active website or online service.
The world of malware has a new rising star - and that's a big problem
A fast-spreading malware-as-a-service offering could be providing an alternative to other well-known malware loaders like Emotet and BazarLoader, experts have warned.
Buer was first discovered in August 2019, when it was used to compromise Windows PCs, acting as a gateway for further attacks to follow.
Buer comes with bot functionality, specific to each download. The bots can be configured depending on a variety of filters, including whether the infected machine is 32 or 64 bits, the country where the exploit is taking place and what specific tasks are required.
https://www.techradar.com/uk/news/the-world-of-malware-has-a-new-rising-star-and-thats-a-problem
Akamai sees doubling in malicious internet traffic as remote world’s bad actors' boom, too
Akamai Technologies’ CEO Tom Leighton is impressed by the amazing traffic levels on the internet during the coronavirus pandemic, and the world technology infrastructure’s ability to handle it. But during the stay-at-home boom, the web and cyber security expert also has been closely watching a boom in bad actors.
With so many people working from home, hackers are taking advantage, and massively increasing the number of attacks as daily routine changes caused by the pandemic are prolonged and become potentially permanent.
Vulnerabilities
Microsoft warns of ongoing attacks using Windows Zerologon flaw
Microsoft today warned that threat actors are continuing to actively exploit systems unpatched against the ZeroLogon privilege escalation vulnerability in the Netlogon Remote Protocol (MS-NRPC).
Oracle WebLogic Server RCE Flaw Under Active Attack
The flaw in the console component of the WebLogic Server, CVE-2020-14882, is under active attack, researchers warn.
If an organization hasn’t updated their Oracle WebLogic servers to protect them against a recently disclosed RCE flaw, researchers have a dire warning: “Assume it has been compromised.”
https://threatpost.com/oracle-weblogic-server-rce-flaw-attack/160723/
This CMS cyberattack has affected thousands of sites worldwide
Security researchers have tracked and analysed a highly sophisticated botnet which they believe to be responsible for infecting hundreds of thousands of websites by attacking their content management system (CMS) platforms.
The botnet, named Kashmir Black, has been in operation since November of last year and while it started out small, it has now evolved into a sophisticated operation capable of attacking thousands of sites each day.
https://www.techradar.com/news/this-cms-cyberattack-has-affected-thousands-of-sites-worldwide
Cisco routers have another high-risk vulnerability
A security vulnerability found in a number of its carrier-grade routers is actively being exploited in the wild by cyber criminals.
The vulnerability affects ASR 9000 series routers, iOS XRv 9000 router and the 540, 560, 1000, 5000, 5500 and 6000 series routers from its Network Convergence System (NCS) line.
https://www.techradar.com/news/cisco-routers-have-another-high-risk-vulnerability
Other News
Security scam hacker ogled 722 women via webcams
A computer hacker who used webcams to watch women undressing and having sex faces extradition to the US.
Christopher Taylor spied on 772 victims in 39 countries — including 52 in the UK — from his Wigan home.
The labourer, 57, tricked the women into downloading software that allowed him to take control of their webcams, Westminster magistrates’ court heard.
https://www.metro.news/security-scam-hacker-ogled-772-women-via-webcams/2199001/
Amazon Discloses Security Incident Involving Customers’ Email Addresses
Amazon informed some of its customers about a security incident that involved the unauthorized disclosure of their email addresses.
News of the security incident emerged over the weekend of October 23 when multiple users took to Twitter to voice their confusion over an email they had received from Amazon.
In an email notification the tech giant explained that it had fired an employee after they unlawfully disclosed some customers’ email addresses to a third party.
'Act of War' Clause Could Nix Cyber Insurance Payouts
Companies relying on their business interruption or property insurance policies to cover ransomware attacks and other cyber damages are running the risk of not having coverage during a major attack if insurers are successful in shielding themselves using the ubiquitous "act of war" clause, according to cyber security and insurance experts.
Therapy patients blackmailed for cash after clinic data breach
Many patients of a large psychotherapy clinic in Finland have been contacted individually by a blackmailer, after their data was stolen.
The data appears to have included personal identification records and notes about what was discussed in therapy sessions.
As usual, contact us to help assess where your risks lie and to ensure you are doing all you can do to keep you and your business secure.
Look out for our weekly ‘Cyber Tip Tuesday’ video blog and on our YouTube channel.
You can also follow us on Facebook, Twitter and LinkedIn.
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
Cyber Weekly Flash Briefing 25 September 2020: GFSC consult on new Cyber Rules; FinCEN leak exposes poor data security; Zerologon attacks detected; ransomware gang behind German hospital death
Cyber Weekly Flash Briefing 25 September 2020: GFSC consulting on new Cyber Rules; Leaked FinCEN files expose poor data security; Microsoft detects active Zerologon attacks; ransomware crew fingered for German hospital death; malware that steals your most sensitive data on the rise; Ransomware is evolving; top threats inside malicious emails; Credential Stuffing behind Recent Attacks
Links to articles are for interest and awareness and linking to or reposting external content does not endorse any service or product, likewise we are not responsible for the security of external links.
GFSC new Cyber Rules and Guidance out for consultation
The GFSC have put the Cyber Security Rules and Guidance Consultation Paper up on their website and consultation hub.
Why this matters:
The new rules and accompanying guidance came out of the 18 month thematic review which ended last year, which found that regulated financial service firms within the Bailiwick of Guernsey were not taking risks from cyber threats seriously enough and were lacking in appropriate protections and controls. These new rules seek to rectify this but many firms on the Island are going to have to do work to become compliant, especially around their ability to monitor for and detect unusual activity that could be indicative of a actual or attempted intrusion or breach.
The rules and guidance can be found here:
Leaked FinCEN files expose poor data security
Leaked documents, dubbed the “FinCEN Files,” describe global money laundering of $2 trillion processed by many of the world’s biggest banks between 2000 and 2017. The reveal illuminates the struggle for the financial industry and government to provide ironclad data protection.
“This sensational and unprecedented leak clearly demonstrates a wide spectrum of data protection weaknesses in the governmental sector, affecting even the most developed Western countries,” Ilia Kolochenko, founder and CEO of ImmuniWeb, said of the files.
“From a cybersecurity standpoint, we may expect a growing lack of trust to governmental agencies, which on one side have quasi-unlimited access to the most sensitive data of the largest organisations, while cannot duly safeguard this data on the other side,” he said.
The latest disclosure exposing apparently insufficient attempts by the public and private sectors to curb corruption came to light in a BuzzFeed News report which detailed more than 2,500 reported cases, including 2,100 Suspicious Activity Reports (SAR) filed by financial institutions with the U.S. Treasury Department’s Financial Crimes Enforcement Network (FinCEN).
JPMorgan Chase, Citigroup, Bank of America, Deutsche Bank, HSBC and Standard Chartered are among the financial institutions cited in the leaked files as processing dirty money around the world. The documents may have come from a whistleblower or insider at FinCEN. The International Consortium of Investigative Journalists (ICIJ), which represents 108 news organizations in 88 countries, is conducting a probe of the matter.
Why this matters:
Other similar investigative reports on similar wrongdoing focused single financial, tax or legal institutions, such as the 2017 Panama Papers emanating from clients of the law firm Mossack Fonseca. But the FinCEN docs reveal that a wide array of people from oligarchs and corrupt politicians to drug dealers and organised crime throughout the world know how to circumvent the system’s supposed checks and balances.
Read more: https://www.scmagazine.com/home/security-news/leaked-fincen-files-expose-poor-data-security/
Microsoft says it detected active attacks leveraging Zerologon vulnerability
Hackers are actively exploiting the Zerologon vulnerability in real-world attacks, Microsoft's security intelligence team said this week.
The attacks were expected to happen, according to security industry experts.
Multiple versions of weaponized proof-of-concept exploit code have been published online in freely downloadable form since details about the Zerologon vulnerability were revealed a week ago.
The first proof-of-concept exploit was published hours after the explanatory blog post, confirming initial analysis that the Zerologon bug is easy to exploit, even by low-skilled threat actors.
Why this matters:
Put simply the Zerologon bug is a vulnerability in Netlogon, the protocol used by Windows systems to authenticate against a Windows Server running as a domain controller. Exploiting the Zerologon bug can allow hackers to take over the domain controller, and inherently a company's internal network.
Zerologon was described by many as the most dangerous bug revealed this year. US federal agencies were given three days to patch domain controllers or disconnect them from federal networks.
As several security experts have recommended since Microsoft revealed the attacks, companies that have their domain controller exposed on the internet should take systems offline to patch them.
These internet-reachable servers are particularly vulnerable as attacks can be mounted directly, without the hacker first needing a foothold on internal systems.
Doppelpaymer ransomware crew fingered for attack on German hospital that caused death of a patient
The Doppelpaymer ransomware gang were behind the cyber-attack on a German hospital that led to one patient's death, according to local sources.
A German newspaper carried a report that Doppelpaymer's eponymous ransomware had been introduced to the University Hospital Düsseldorf's network through a vulnerable Citrix product.
That ransomware infection, activated last week, is said by local prosecutors to have led to the death of one patient who the hospital was unable to treat on arrival. She died in an ambulance while being transported to another medical facility with functioning systems.
Why this matters:
According to a report handed to the provincial government of North Rhine-Westphalia and seen by the German Press Association (DPA), the ransomware's loader had been lurking on the hospital's network since December 2019, the same month a patch was issued by Citrix for CVE-2019-19781 – the same vuln exploited to hit the hospital.
Whilst this is the first time a loss of life has been directly attributed to ransomware the threats are increasing all the time.
Vulnerabilities must be patched as soon as possible to stop known vulnerabilities from being used in attacks.
Read more: https://www.theregister.com/2020/09/23/doppelpaymer_german_hospital_ransomware/
“LokiBot,” the malware that steals your most sensitive data, is on the rise
Agencies in the US have reported seeing a big uptick in infections coming from LokiBot, an open source DIY malware package for Windows that’s openly sold or traded for free in underground forums. It steals passwords and cryptocurrency wallets, and it can also download and install new malware.
The increase was measured by an automated intrusion-detection system for collecting, correlating, analysing, and sharing computer security information.
US cyber agency CISA observed a notable increase in the use of LokiBot malware by malicious cyber actors since July 2020 according to an alert issued this week.
Why this matters:
While not quite as prevalent or noxious as the Emotet malware, LokiBot remains a serious and widespread menace. The infostealer spreads through a variety of methods, including malicious email attachments, exploitation of software vulnerabilities, and trojans sneaked into pirated or free apps. Its simple interface and reliable codebase make it attractive to a wide range of crooks, including those who are new to cybercrime and have few technical skills.
Ransomware is evolving, but the key to preventing attacks remains the same
Ransomware attacks are getting more aggressive according to a senior figure at Europe's law enforcement agency, but there are simple steps which organisations can follow to protect themselves – and their employees – from falling victim to attacks.
"Ransomware is one of the main threats," said the head of operations at Europol's European Cybercrime Centre (EC3). Europol supports the 27 EU member states in their fight against terrorism, cybercrime and other serious and organised forms of crime.
"Criminals behind ransomware attacks are adapting their attack vectors, they're more aggressive than in the past – they're not only encrypting the files, they're also exfiltrating data and making it available," he explained. "From a law enforcement perspective, we have been monitoring this evolution."
Why this matters:
This year has seen a rise in ransomware attacks where cyber criminals aren't just encrypting the networks of victims and demanding six-figure bitcoin payment to return the files, but they're also threatening to publish sensitive corporate information and other stolen data if the victim doesn't pay the ransom.
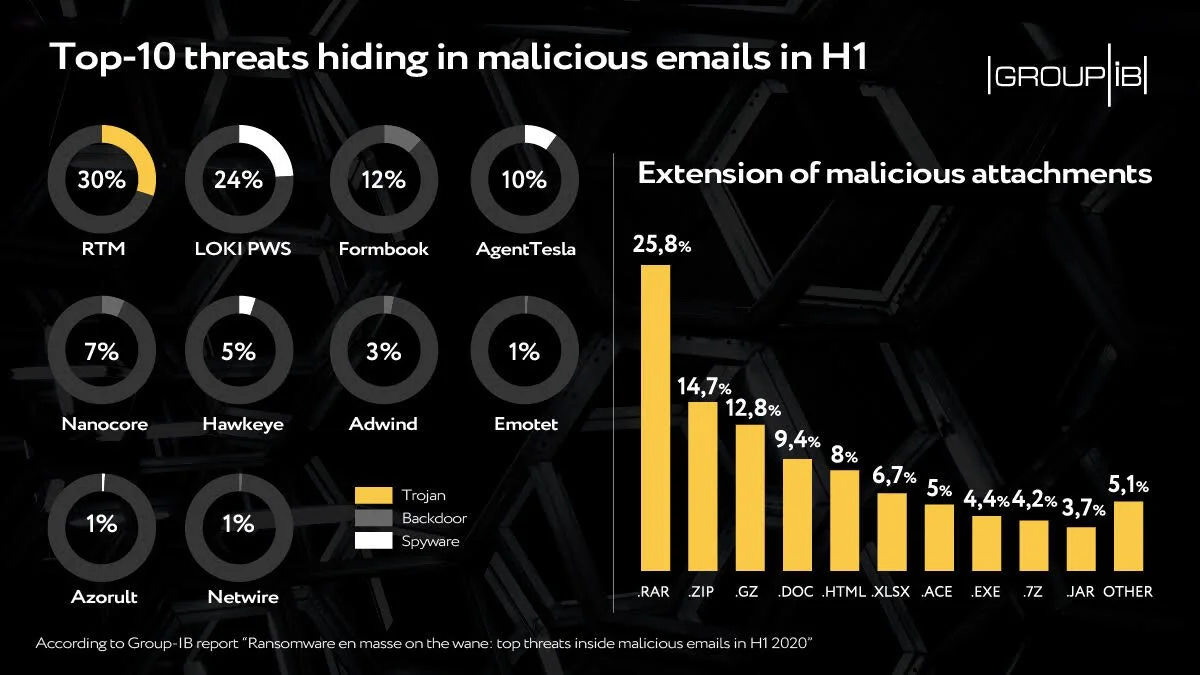
A look at the top threats inside malicious emails
Web-phishing targeting various online services almost doubled during the COVID-19 pandemic: it accounted for 46 percent of the total number of fake web pages, Group-IB reveals.
Ransomware, the headliner of the previous half-year, walked off stage: only 1 percent of emails analysed contained this kind of malware. Every third email, meanwhile, contained spyware, which is used by threat actors to steal payment data or other sensitive info to then put it on sale in the darknet or blackmail its owner.
Downloaders, intended for the installation of additional malware, and backdoors, granting cybercriminals remote access to victims’ computers, also made it to top-3. They are followed by banking Trojans, whose share in the total amount of malicious attachments showed growth for the first time in a while.
According to the data, in H1 2020 detected malicious emails were:
43 percent of the malicious mails had attachments with spyware or links leading to their downloading
17 percent contained downloaders
16 percent had backdoors
15 percent had banking trojans
Ransomware, which in the second half of 2019 hid in every second malicious email, almost disappeared from the mailboxes in the first six months of this year with a share of less than 1 percent.
Why this matters:
These findings confirm adversaries’ growing interest in Big Game Hunting. Ransomware operators have switched from attacks en masse on individuals to corporate networks. Thus, when attacking large companies, instead of infecting the computer of a separate individual immediately after the compromise, attackers use the infected machine to move laterally in the network, escalate the privileges in the system and distribute ransomware on as many hosts as possible.
Read more: https://www.helpnetsecurity.com/2020/09/21/top-threats-inside-malicious-emails/
Credential Stuffing: the Culprit of Recent Attacks
A year ago, researchers found that 2.2 billion leaked records, known as Collection 1-5, were being passed around by hackers. This ‘mega leak’ included 1.2 billion unique email addresses and password combinations, 773 million unique email addresses and 21 million plaintext passwords. With this treasure trove, hackers can simply test email and password combinations on different sites, hoping that a user has reused one. This popular technique is known as credential stuffing and is the culprit of many recent data breaches.
There are only a few months left of 2020 but this year has seen its fair share of major data breaches including:
Marriott International experienced another mega breach, when it was still recovering from the 2018 data breach that exposed approximately 339 million customer records
Zoom became a new favourite for hackers due to the remote working mandated in many parts of the world - in early April Zoom fell victim to a credential stuffing attack, which resulted in 500,000 of Zoom’s usernames and passwords being exposed on the Dark Web.
GoDaddy, the world’s largest domain registrar confirmed in April that credentials of 28,000 of its customer web hosting accounts were compromised in a security incident back in October 2019.
Nintendo - in March, users reported unauthorised logins to their accounts and charges for digital items without their permission. In June Nintendo advised that approximately 300,000 accounts were affected by the breach, resulting in the compromise of personal identifiable information such as email address, date of birth, country and gender.
Why this matters:
It has become evident that many of the recent data breaches were the result of credential stuffing attacks leveraging compromised passwords or passphrases. Credential stuffing attacks are automated hacks where stolen usernames and password combinations are thrown at the login process of various websites in an effort to break in. With billions of compromised credentials already circulating the Dark Web, credential stuffing attacks can be carried out with relative ease and with a 1-3% success rate.
When the account of an employee is compromised, hackers can gain access to sensitive data that organisation has collected, and sell it on the Dark Web. The stolen data, often including login credentials, can then be used to infiltrate other organisations’ systems which creates a never-ending cycle.
This is why the LinkedIn breach was blamed for several secondary compromises due to users recycling their exposed LinkedIn passwords on other sites.
Read more: https://www.infosecurity-magazine.com/blogs/credential-stuffing-recent-attacks/